Table of Contents
ToggleFrom the emergence of new worms, malware, viruses, and ransomware to the high profile of international conflicts, terrorist organizations, etc., data breaching has been a major pain point in various institutes. Millions of organizations across the globe are paying lumpsum to cybercriminals to seize crucial information and data and in turn, blackmail the owners for billions of dollars. Ethical Hacking has, therefore, become one of the most vital wings of every industry that can protect the data files from malware injection and, thereby, fall victim to cybercriminals. Nearly 70% of Iran’s gas stations went out of service on Dec 18, 2023, following possible sabotage — a reference to cyberattacks, Iranian state TV reported.
Image source: livemint.com
What is Ethical Hacking?
If you are down with a fever, you usually take paracetamol or something similar. It’s more like you’re taking an antidote to get rid of your sickness. But have you ever thought about what you could have done that could have saved you from catching a fever? Such protective measures are similar to the concept of Ethical Hacking.
Ethical hacking is when a person, also known as an Ethical Hacker, intentionally tries to break into a computer system to identify what the weak points are. The primary goal is to discover any potential problems that cybercriminals could exploit. The information gained from this process is then used to make the computer system stronger and better protected against potential attacks.
Usually, an Ethical Hacker Answers the following questions:
- What kind of vulnerabilities does an attacker see?
- What can an attacker do with the information?
- How many people noticed the attempted hack?
- What is the best way to fix the vulnerability?
Let’s see what Jay Bavisi, the CEO of EC Council has to say about Ethical Hacking.
Image source: eccouncil.org
With data breaches being a common scenario, people are inclined towards learning and upskilling in Ethical Hacking. Ethical hacking is not only meant for government institutions, but professionals in finance, healthcare, education, IT, etc., are also looking for proper guidance. A certified ethical hacker is considered to be one of the most precious assets of an organization. We’ll thoroughly discuss the responsibilities of an ethical hacker in the later chapters.
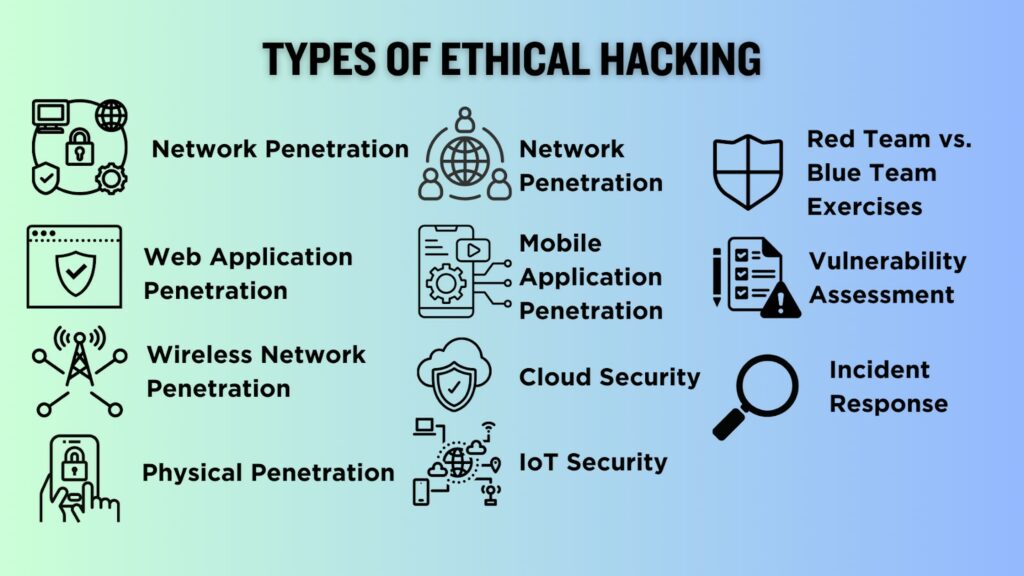
Types of Ethical Hacking
Now that we have already discussed how cybercriminals exploit organizations, these are the following types of Ethical Hacking performed by Ethical Hackers to protect crucial and confidential information.
There are various types of ethical hacking, each focusing on specific areas of cybersecurity. Here are some common types:
1. Network Penetration Testing
Involves assessing the security of a network to identify vulnerabilities that malicious hackers could exploit. This type of testing aims to strengthen the overall network security.
2. Web Application Penetration Testing
Focuses on assessing the security of web applications, identifying vulnerabilities such as SQL injection, cross-site scripting (XSS), and other web-related vulnerabilities.
3. Wireless Network Penetration Testing
Image source: semanticscholar.org
Evaluate the security of wireless networks, including Wi-Fi networks, to identify weaknesses that unauthorized users could exploit. This type of testing helps ensure the confidentiality and integrity of wireless communications.
4. Social Engineering Testing
Involves simulating attacks that exploit human psychology and behavior to gain access to sensitive information. This can include phishing campaigns, pretexting, and other methods to test the organization’s resistance to social engineering attacks.
5. Mobile Application Penetration Testing
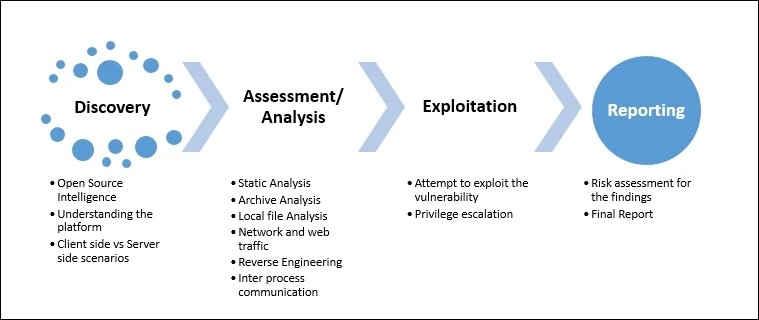
Image source: subscription.packtpub.com
Assesses the security of mobile applications to identify vulnerabilities that could be exploited on mobile platforms. This is crucial as mobile apps often handle sensitive user data.
6. Physical Penetration Testing
Evaluates the physical security of an organization by attempting to gain unauthorized access to buildings, offices, or data centers. This type of testing assesses the effectiveness of physical security measures.
7. Cloud Security Testing
Focuses on evaluating the security of cloud-based services and infrastructure. This includes assessing configurations, access controls, and other security aspects related to cloud computing.
8. IoT (Internet of Things) Security Testing
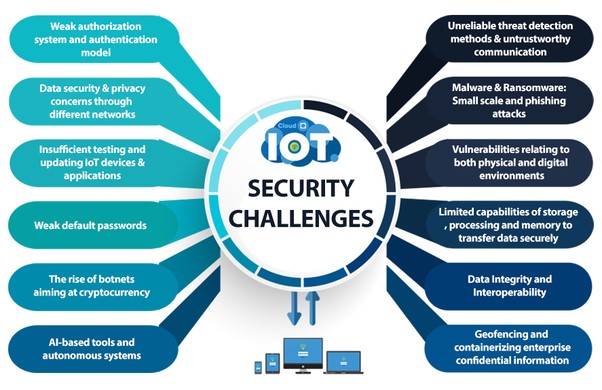
Image source: themachinist.in
Assesses the security of Internet of Things devices and systems. IoT security testing ensures that connected devices are secure and do not pose risks to the overall network.
9. Red Team vs. Blue Team Exercises
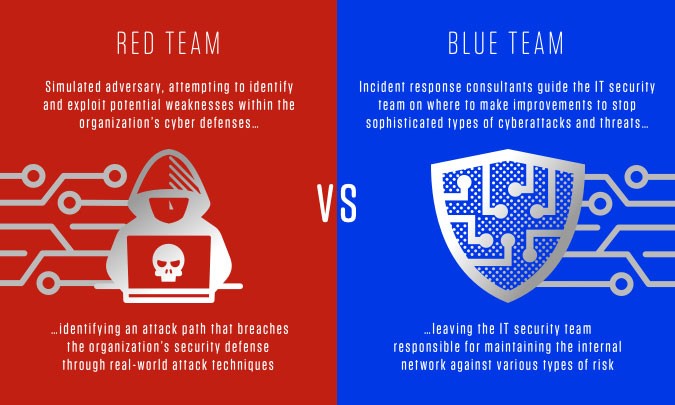
Image source: crowdstrike.com
Involves simulated attacks (Red Team) against a system defended by security professionals (Blue Team). This type of testing provides a comprehensive assessment of an organization’s overall security posture.
10. Vulnerability Assessment
A broader approach that involves identifying, classifying, and prioritizing vulnerabilities in a system. While not strictly hacking, it forms the foundation for ethical hacking activities.
11. Incident Response Testing
Assesses an organization’s ability to detect and respond to security incidents. This type of testing helps organizations improve their incident response capabilities.
What are the Five Phases of Ethical Hacking?
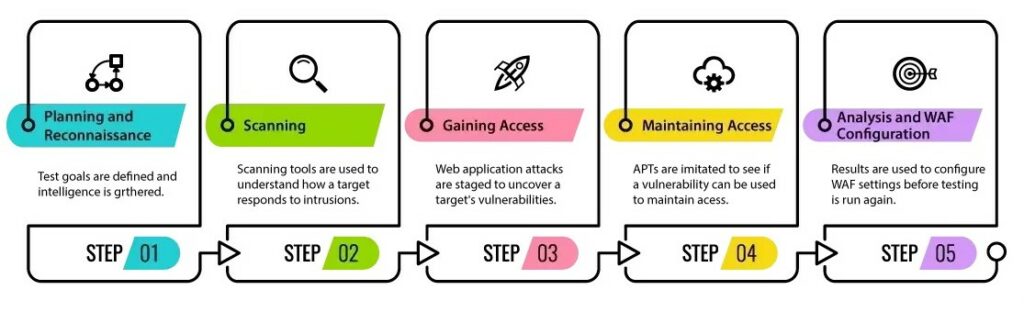
Image source: eccouncil.org
A Certified Ethical Hacker is well aware of the five prime phases of Ethical Hacking. The five phases of ethical hacking, often referred to as the hacking or penetration testing lifecycle, provide a structured approach to conducting ethical hacking activities. These phases help ethical hackers systematically identify and address security vulnerabilities. The five phases are:
- Planning and Reconnaissance- In this initial phase, ethical hackers gather information about the target system, network, or organization. This may involve passive reconnaissance, such as collecting publicly available information from websites, social media, or domain registries. Active reconnaissance may include network scanning to discover live hosts, open ports, and services.
- Scanning (Enumeration)- Once information is gathered, the ethical hacker proceeds to the scanning phase. This involves actively probing the target system or network to identify live hosts, services running on those hosts, and potential vulnerabilities. Tools like Nmap or Nessus may be used to conduct detailed scans and enumerate the target.
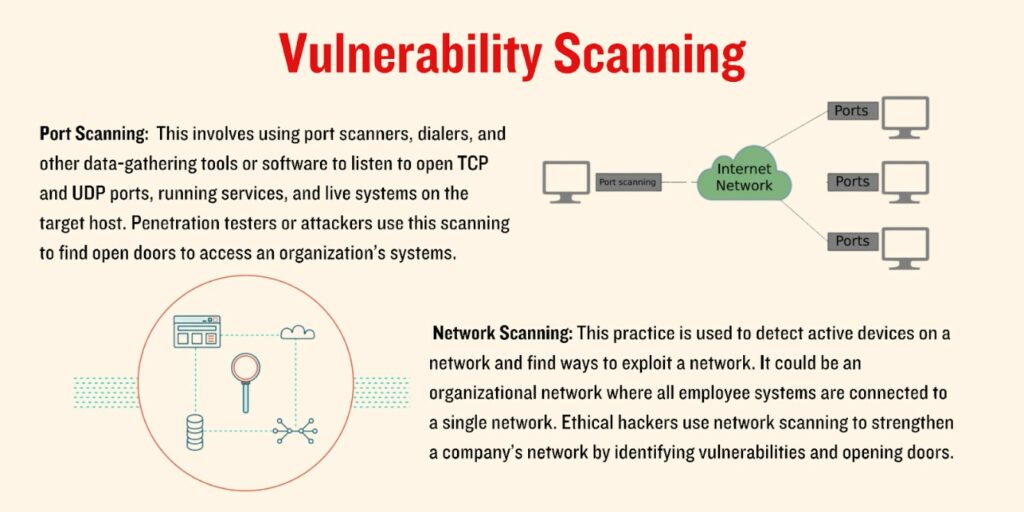
- Gaining Access (Exploitation)- In the exploitation phase, ethical hackers attempt to exploit vulnerabilities identified during the scanning phase. This may involve using known exploits, custom scripts, or tools to gain unauthorized access to the target system. The goal is to understand the extent to which a system can be compromised and to provide recommendations for mitigating the identified vulnerabilities.
- Maintaining Access (Post-exploitation)- After gaining initial access, ethical hackers aim to maintain their presence on the target system. This involves creating backdoors, establishing persistence, and exploring the system further to uncover additional vulnerabilities or sensitive information. Understanding the potential for long-term access helps organizations address weaknesses in their security posture.
- Clearing Access- The final phase involves analyzing the results of the ethical hacking activities and preparing a comprehensive report. Ethical hackers document the vulnerabilities discovered, the methods used to exploit them, and recommendations for remediation. The report provides actionable insights for organizations to enhance their security measures and mitigate potential risks.
In a nutshell, the entire process along with its various steps looks like this:
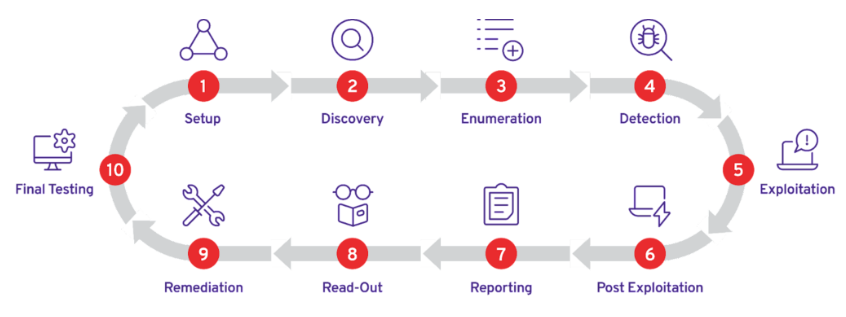
Image Source: plextrac.com
How many types of Ethical Hackers are there?
Before going into that detail, let’s check a quick fact:
- 43% of hackers target smaller businesses.
- A hacker attack happens every 39 seconds (approx)
- The total number of connected IoT devices will have reached 75 billion by 2025

Image source: nwkings.com
1. White-Hat Hackers
These are Ethical Hackers or computer security experts who specialize in testing methods like penetration testing to ensure an organization’s information systems are secure.
2. Black-Hat Hackers
A Black Hat Hacker is someone with advanced computer knowledge who breaches or bypasses internet security for malicious reasons or personal gain.
3. Gray-Hat Hackers
Gray Hat Hackers may violate ethical standards but lack the malicious intent associated with black hat hackers.
4. Green Hat Hackers
A green hat hacker is like a beginner in the hacking world. They might not know much about how a company’s security works. They could be new and still learning about how the internet and computer systems function.
5. Blue Hat Hackers
Blue hat hackers are hired by companies to test their systems before they are launched. They look for any problems or weak points so they can be fixed before the system goes live.
6. Red Hat Hackers
Red hat hackers focus on hacking into Linux systems. They are like online vigilantes, working to stop other hackers. While they share some goals with white hat hackers, their methods can be quite different.
7. State/Nation Sponsored Hackers
These hackers work for the government and have permission to hack. They are hired to disrupt or compromise other governments, organizations, or individuals. Their goal is to access important data or intelligence that could have a big impact internationally.
8. Script Kiddies
These hackers lack significant training and only use basic techniques or tools, often without a full understanding of their actions.
Benefits of Ethical Hacking
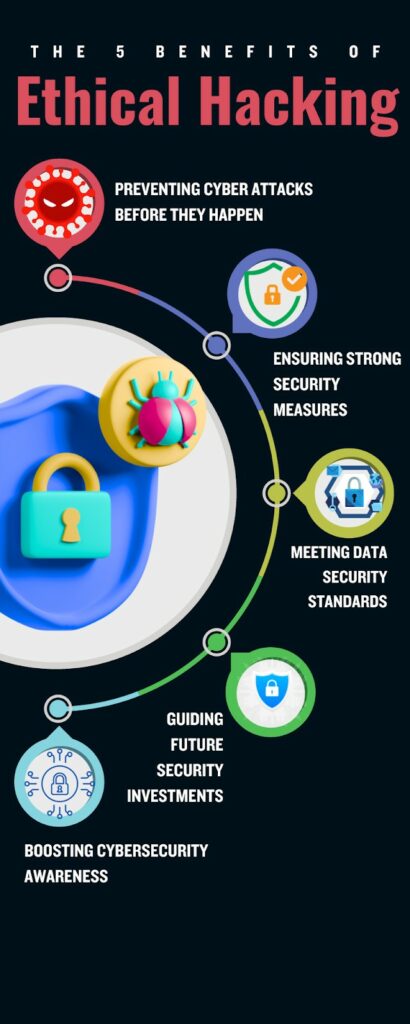
1. Preventing Cyber Attacks Before They Happen
Ethical hacking lets you be proactive in securing your business from cyber threats by fixing vulnerabilities before they’re exploited. This helps safeguard your sensitive data and prevents major damage that could be caused by cybercriminals.
2. Ensuring Strong Security Measures
When you hire an ethical hacker for your business systems, they provide valuable feedback and suggestions to enhance your security. This independent assurance helps you strengthen your defenses against potential threats.
3. Meeting Data Security Standards
Ethical hacking ensures that your business complies with evolving cybersecurity requirements like GDPR and ISO 27001. By doing so, you avoid penalties for non-compliance and maintain a secure environment for your data.
4. Guiding Future Security Investments
By identifying vulnerabilities, ethical hacking gives you insights into areas that need improvement. This information guides your future security investments, ensuring you focus on the right areas to enhance overall cybersecurity.
5. Boosting Cybersecurity Awareness
Ethical hacking demonstrates your ongoing commitment to security, both to your customers and staff. Ethical hackers can educate your team about the latest methods used by cybercriminals, increasing overall awareness of cybersecurity risks.
Conclusion
So, to wrap up, businesses and organizations are investing a lot in ethical hacking. Ethical hacking plays a crucial role in fortifying your business against cyber threats. Furthermore, the insights gained from Ethical Hacking guide future investments in cybersecurity, ensuring resources are directed where they are most needed. Lastly, by engaging in Ethical Hacking, you not only demonstrate a commitment to security but also enhance awareness among both customers and staff about the ever-present risks in the digital landscape. If you’re aspiring to be a certified Ethical Hacker, EC-Council accredited CEH certification will help you grow in your career.
