Table of Contents
ToggleAccording to Statista, cybercrime will hit the global economy by more than 20 trillion U.S. dollars by 2026, which surpasses $8 trillion in 2022, i.e., more than the predicted value. Experts are expecting that this figure in 2026 will be almost or more than 1.5x than that in 2022 and the value is exponentially growing by approximately 5% every year! Geopolitical threats, deepfake AI, and many other aspects are continuously posing threats in the digital world and hence, cybercrimes are skyrocketing. To combat such odds, the entire globe is looking for efficient and certified Ethical Hackers, and consequently, their demand in the job market is quite hyped. This blog will discuss ethical hacker salary structure explicitly.
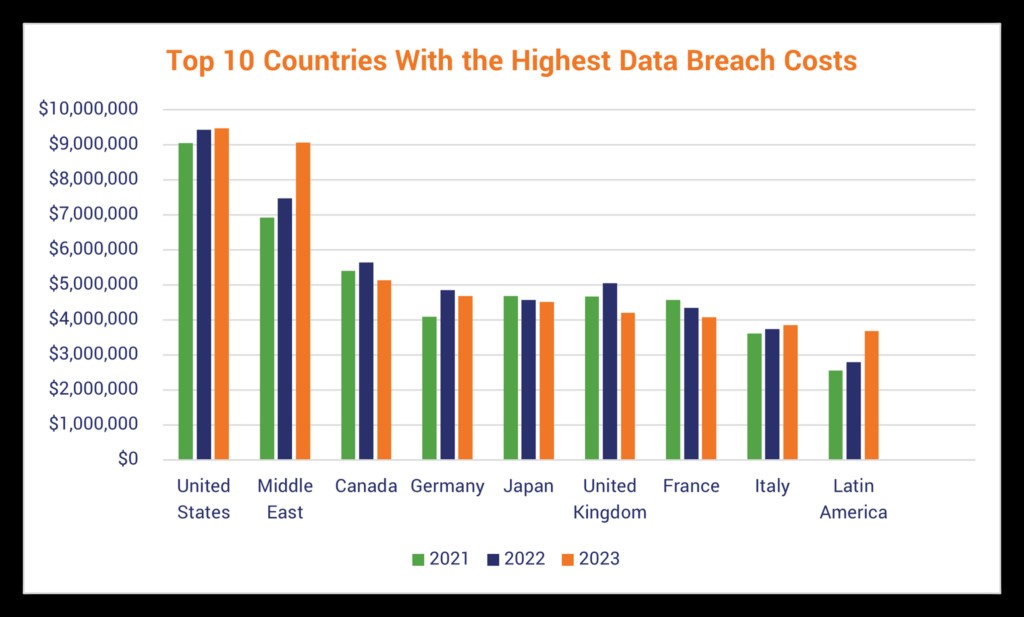
Image source: thesslstore.com
Why Certified Ethical Hackers are in Demand?
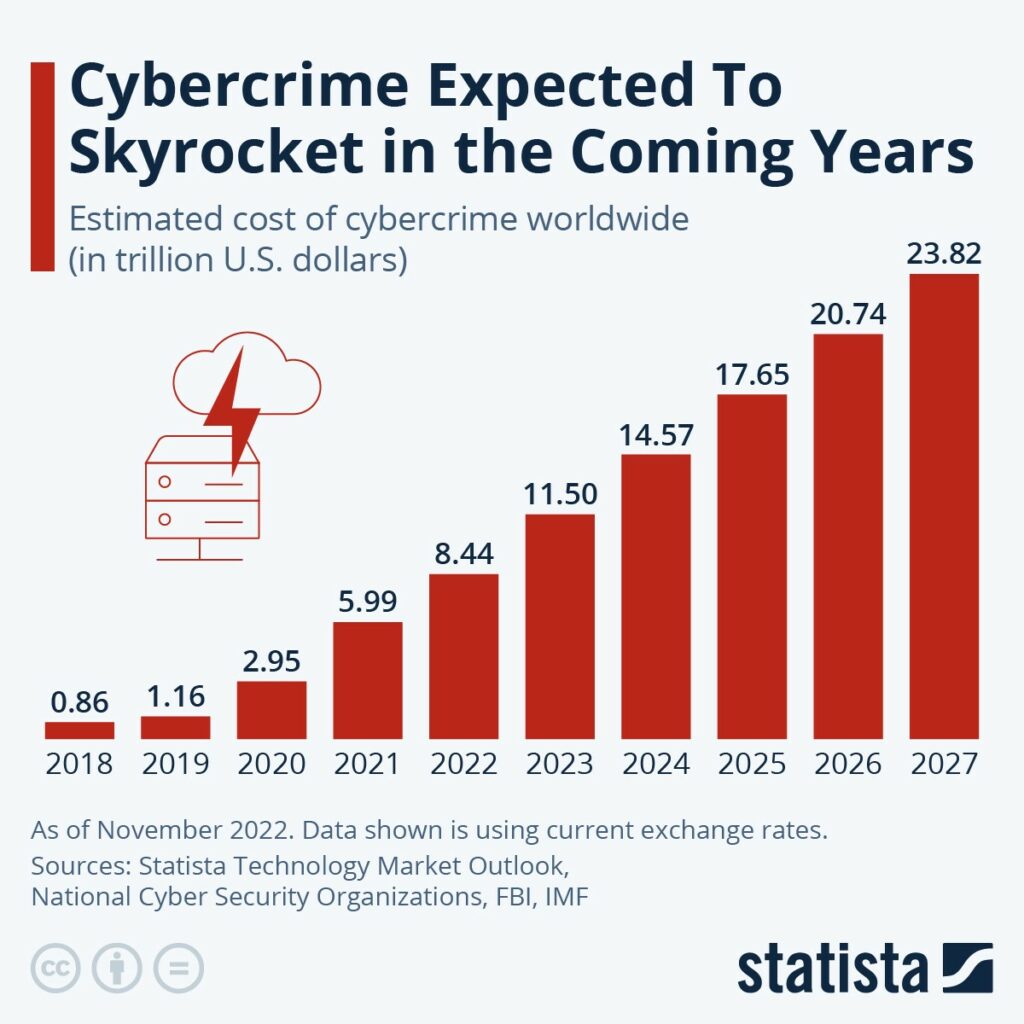
Image source: statista.com
If you carefully observe this image, you will see how drastically cybercrime proliferates. Ethical hackers, possessing expertise in systems and network security, play a crucial role in thwarting cyber-attacks, placing them at the forefront of efforts to prevent such incidents. Needless to say, this is the primary reason why there is a huge vacancy for the roles of Ethical Hackers
These are the major responsibilities of a certified ethical hacker
- Figure out and categorize system and network stuff.
- Decide how important each thing is.
- Find possible problems and threats.
- Make a plan for dealing with big problems first.
- Come up with ways to lessen the damage if there’s an attack.
- Test different things like websites, hardware, and software.
- Keep everything updated with the latest fixes.
- Think up new strategies to stop hackers and reduce threats.
- Make reports about security and save them for reference.
- Keep an eye on system and network things to catch possible problems.
- Create and enforce security rules.
An efficient, ethical hacker helps organizations stay alert by tracking what scammers are planning and how they may sabotage. An ethical hacker protects the organization from the following major issues:
Image source: edureka.co
With the dark web being a massive point of attraction, cybercriminals are constant members of this malicious platform. Cybercriminals use the dark web to buy and sell malware, exploit kits, and cyberattack services. They weaponize all these to strike victims, including businesses, governments, utilities, and essential service providers. Governments are spending billions of dollars on cybersecurity across the globe.
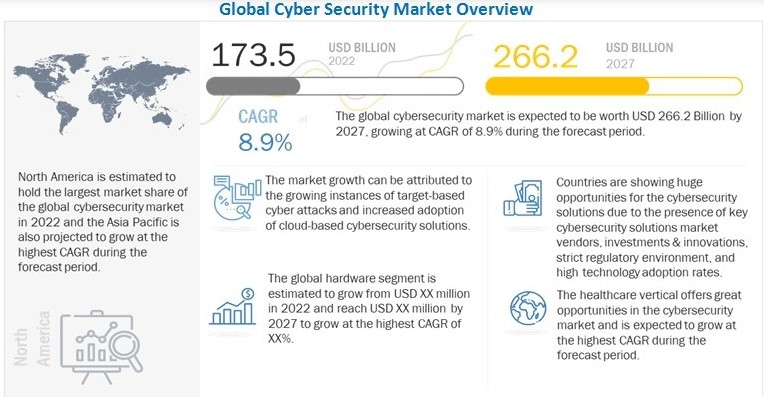
Image source: marketsandmarkets.com
All these data and statistical reports are going in only one direction, i.e., the demand for skilled Ethical Hackers. According to the World Economic Forum, the expected demand for skilled cybersecurity professionals will continue to grow for the foreseeable future as the cybersecurity market becomes worth more than $370 billion by 2029.
What is the Ethical Hacker’s Salary?
As there has been a consistent demand for Ethical Hackers, their salary package is quite lucrative. In 2024, the salary of a certified ethical hacker will be alluring but that also depends upon their level of experience and skill-set. The average annual pay for an Ethical Hacker in the United States is $135,269 per year, which is approximately $65.03 an hour.
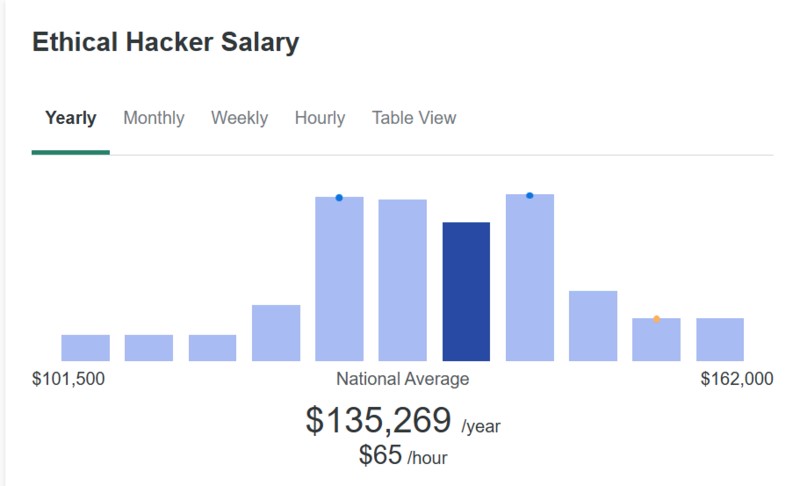
Image source: stationx.net
A certification in Ethical Hacking will reflect immediately in your salary package, as well as, your demand in the job market. Based on Glassdoor’s data, the following is the approximate salary structure of a certified ethical hacker:
- Entry-level ethical hacker salary (0–1 year experience): $89,058
- Intermediate ethical hacker salary (1-3 years experience): $96,814
- Advanced-level ethical hacker salary (4-6 years experience): $109,0
- Expert-level ethical hacker salary (7-9 years experience): $121,620
Ethical Hacker Salary in Foreign Countries
Professionals who are into ethical hacking often go for a CEH V12 Certification that gives them a holistic approach to the world of cybersecurity. They get to know the nitty-gritty of how ethical hacking works in various industries. Besides, they also get an insight into IT Governance and Cybersecurity domains globally. With this Certified Ethical Hacking certification, ethical hackers develop amazing skills and hence, their demand in the job market increases quite a lot.
1. Ethical Hacker Salary in The United States of America (USA)
Cybercriminals in the USA are technically considering the Year-End Sale Season as one of the greatest opportunities to run their fraud games. The FBI has warned the public to be aware of gift cards, coupons, discounts, and other lucrative offers that often become irresistible to many online shoppers.

Image Source: usatoday.com
In the USA, the average salary of a Certified Ethical Hacker is $90k. The image shows how CEHs are being paid in various job roles in the USA.
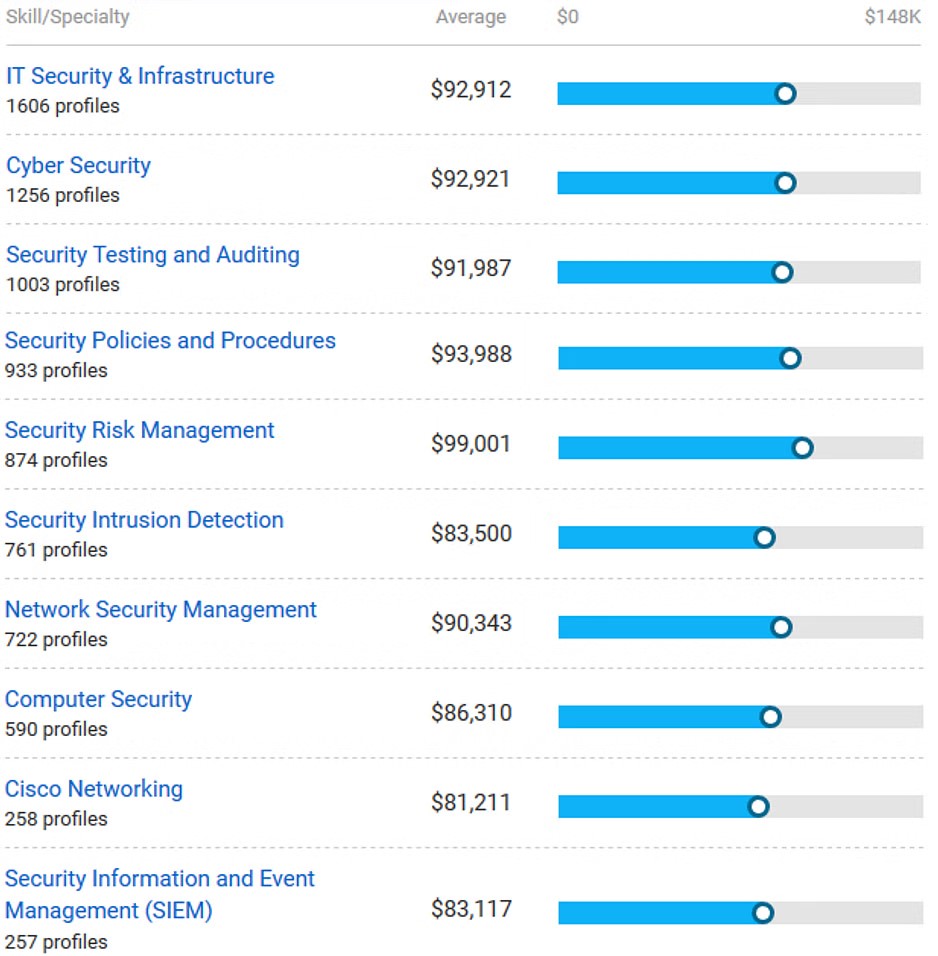
Image source: payscale.com
Companies Hiring Certified Ethical Hackers in the USA:
- Booz, Allen, and Hamilton $67,470 – $101,389
- U.S. Army $32,133 – $86,327
- U.S. Air Force (USAF) $49,029 – $81,490
- General Dynamics Information Technology Inc $59,045 – $104,805
- Lockheed Martin Corp $69,043 – $113,000
Cities where Ethical Hackers are in demand:
- Washington, District of Columbia $67,000 – $126,121
- New York, New York $50,143 – $124,608
- San Antonio, Texas $51,456 – $90,999
- Atlanta, Georgia $49,550 – $110,936
- San Diego, California $76,754 – $121,694
Years of Experience:
- Less than 1 year 3%
- 1-4 years 30%
- 5-9 years 27%
- 10-19 years 30%
- 20 years or more 9%
2. Ethical Hacker Salary in India
With the latest digital transformation and integration of artificial intelligence, there is a surge in cybercrimes. Gurgaon is considered the cyber hub of India and is one of the major locations where cybercrimes and scams are taking place. Scammers are getting arrested and Gurgaon Police is doing their job like a pro but then again, the threats from cybercriminals are not diminishing. The Indian Express published news where Gurgaon Polic captured 7 cyber scammers and traced almost INR 22 cr.
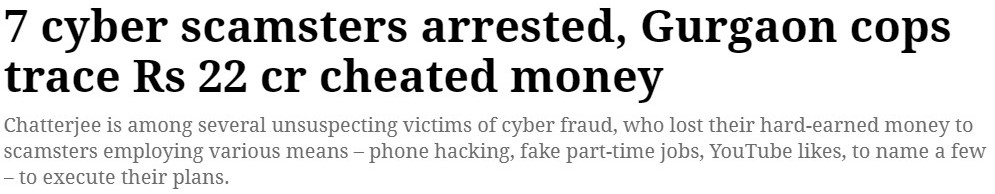
Siddhant Jain, Deputy Police Commissioner (South), said that upon scrutinizing the data from the Indian Cyber Crime Coordination Center (I4C) for the seized mobile phones and SIM cards of the accused, it was revealed Danish and Majid were linked to Rs 18 crore worth of fraud. “175 FIRs are nationally registered, and eight are specific to Haryana. Other accused – Navdeep Kumawat, Krishna Gopal, Mahendra Kumar Sen, and Sachin Nama – are linked to Rs 2.5 crore, with 39 FIRs registered, and three specific to Haryana. Accused Suraj Rana is linked to Rs 1.68 crore, with 28 FIRs across the country and two in Haryana,” he said.
Source: indianexpress.com
The image below shows the job opportunities and estimated salary structure of ethical hackers in India. The Average CEH Salary is INR 599K.
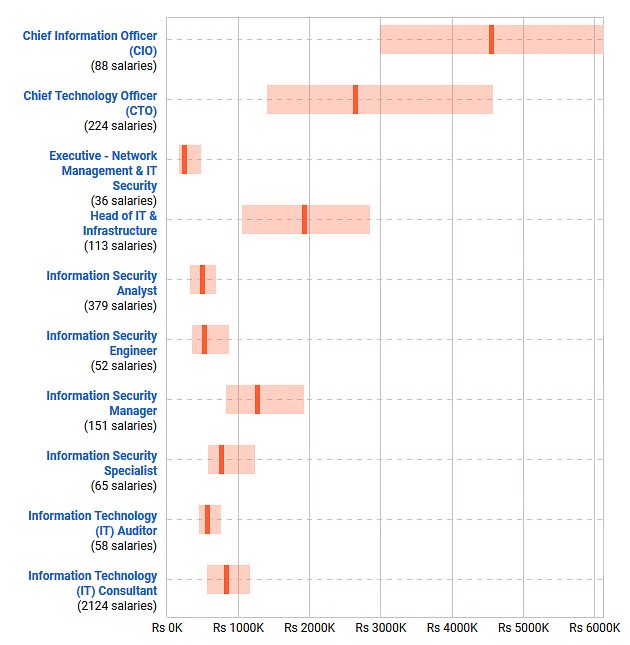
Image source: payscale.com
Companies Hiring Certified Ethical Hackers in India:
- Paladion Networks Rs 214,551 – Rs 509,714
- Wipro Technologies Ltd. Rs 101,980 – Rs 800,000
- Tata Consultancy Services Limited Rs 290,874 – Rs 630,000
- EY (Ernst & Young) Rs 316,266 – Rs 752,553
- Infosys Limited Rs 121,641 – Rs 910,630
Cities where Ethical Hackers are in demand:
- Bangalore, Karnataka Rs 256,635 – Rs 1,133,880
- Mumbai, Maharashtra Rs 218,305 – Rs 1,072,867
- Chennai, Tamil Nadu Rs 241,957 – Rs 913,540
- Pune, Maharashtra Rs 254,028 – Rs 1,043,389
- Hyderabad, Andhra Pradesh Rs 236,718 – Rs 982,635
Years of Experience:
- Less than 1 year 15%
- 1-4 years 48%
- 5-9 years 23%
- 10-19 years 13%
- 20 years or more 1%
3. Ethical Hacker Salary in Australia
Nearly half of all Australians who used the internet in the past year have experienced some type of cybercrime, according to a concerning survey by the Australian Institute of Criminology. The survey, conducted between February and March and with over 13,800 participants, reveals that 47% of respondents reported falling victim to cybercrime in the preceding 12 months. The findings raise alarm about a surge in cybercrime affecting the country.
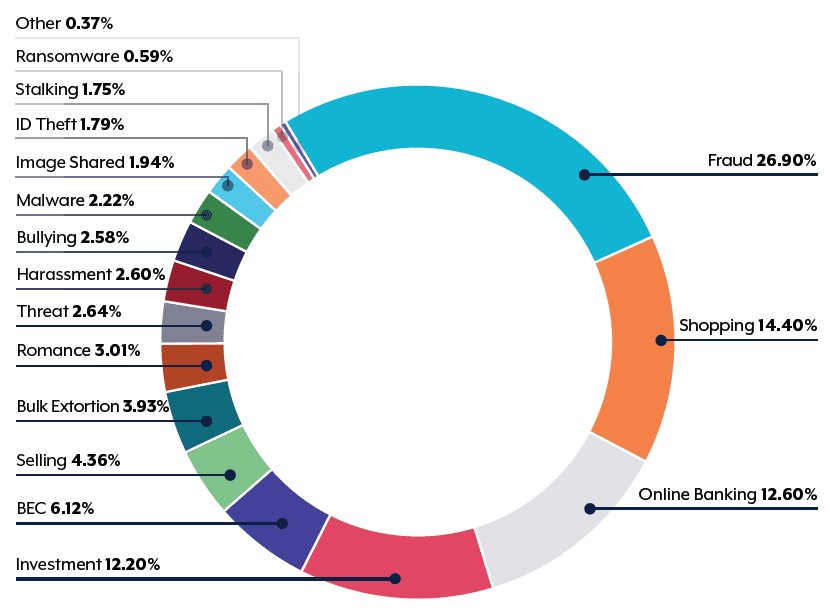
Image source: cyber.gov.au
Cybercrimes in Australia are quite severe and the image above thoroughly points out the verticals where maximum of the scams have happened. This has shaken the entire nation and as a result, the Australian Government is focusing quite heavily on cybersecurity. A report from AustCyber states that Australia has spent approximately $5.6 billion on cybersecurity and by 2024 the value may reach $7.6 billion.
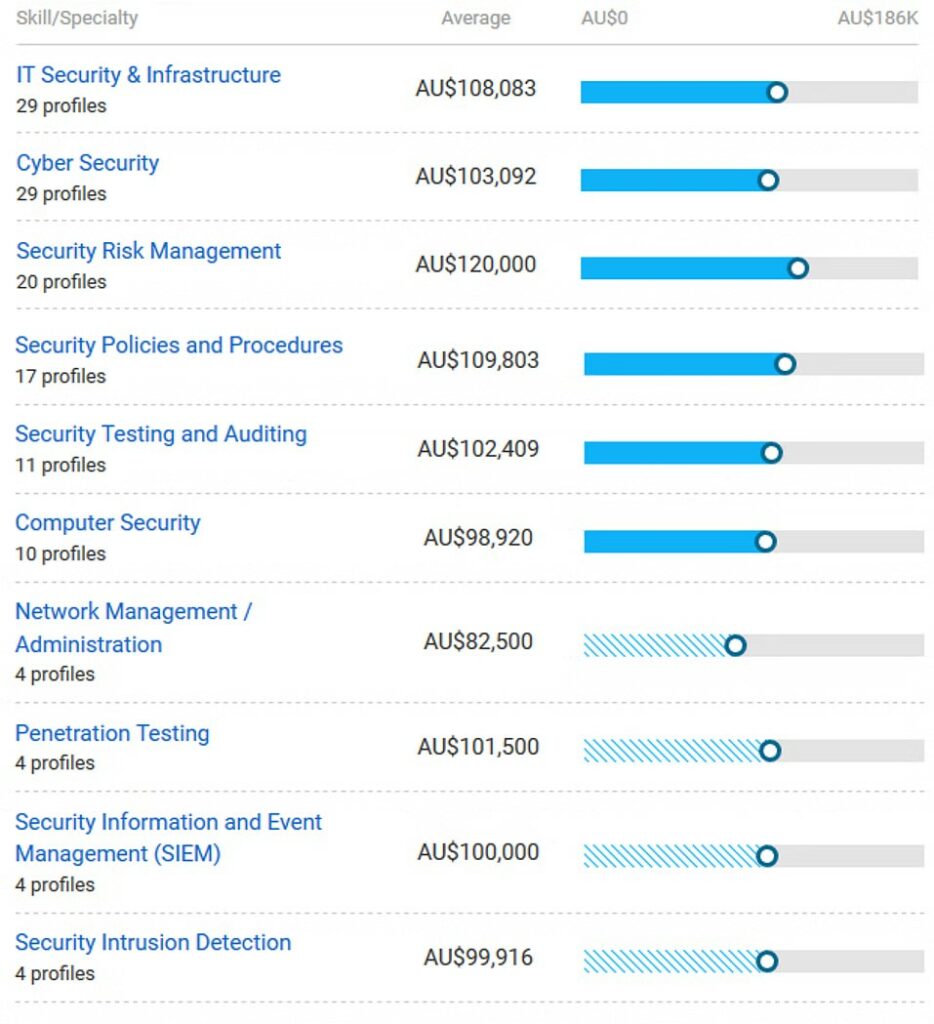
Image source: payscale.com
Companies that are hiring Certified Ethical Hackers in Australia:
- EY (Ernst & Young) AU$125,000
- Deloitte AU$143,364
- The Chemist Warehouse AU$55,000
Cities where Ethical Hackers are in demand:
- Sydney, New South Wales AU$55,284 – AU$133,346
- Melbourne, Victoria AU$53,327 – AU$145,216
Years of Experience:
- Less than 1 year 2%
- 1-4 years 36%
- 5-9 years 30%
- 10-19 years 27%
- 20 years or more 4%
4. Ethical Hacker Salary in UAE
In UAE, cyberattacks are a major pain point. In the past few months, a group of hackers have been trying to steal personal and money-related info from people in the United Arab Emirates. This new research shows that the hackers, known as the Smishing Triad gang, use text messages to trick residents and visitors. They pretend to be UAE authorities and send messages asking for details like home addresses, phone numbers, and credit card info.
The messages work on both Apple and Android phones, and they include a link to a fake website that looks a lot like the official one from the UAE agency that handles residency and foreign affairs, as found by Resecurity researchers. Consequently, the need for ethical hackers in the UAE is increasing consistently. The average CEH Salary in UAE is AED 177K.
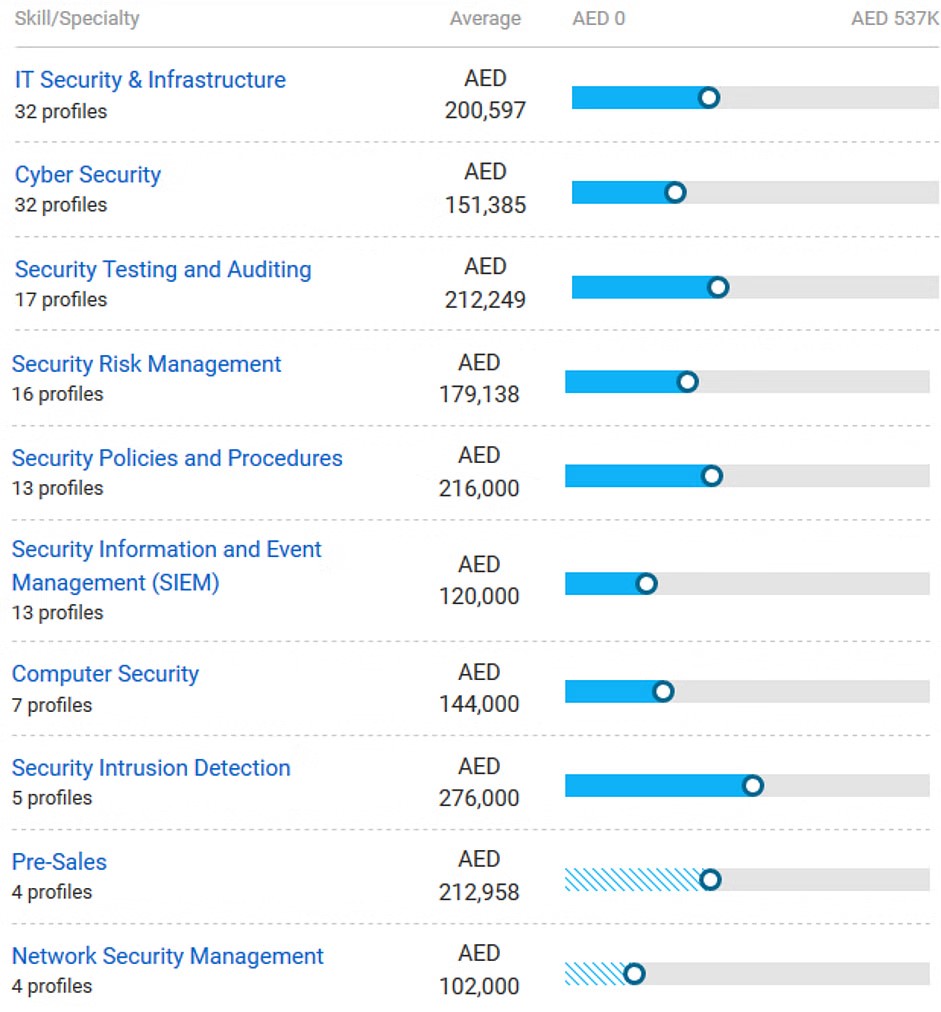
Image source: payscale.com
Companies that are hiring for Certified Ethical Hackers:
- Paladion Networks AED 166,268
- Abu Dhabi Commercial Bank AED 450,000
- Tata Consultancy Services Limited AED 115,800
Cities where Ethical Hackers are in demand:
- Dubai AED 60,678 – AED 301,674
- Abu Dhabi AED 52,586 – AED 305,209
Years of Experience:
- Less than 1 year 4%
- 1-4 years 34%
- 5-9 years 34%
- 10-19 years 26%
- 20 years or more 1%
5. Ethical Hacker Salary in Canada
This report from Reuters shows what happened to Canada in 2022 due to a massive cyber attack.
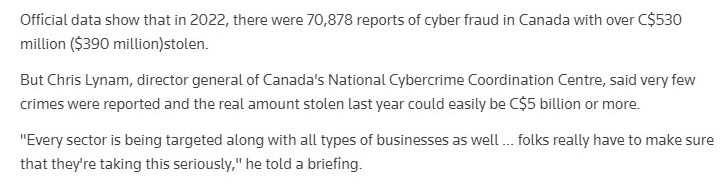
Cyber threats in Canada have not diminished and there’s no scope of it as well. Therefore, organizations are up for working with certified ethical hackers who will be a shield against every cyber attack. Various companies are hiring CEHs and the average salary for certified ethical hackers is C$73K.
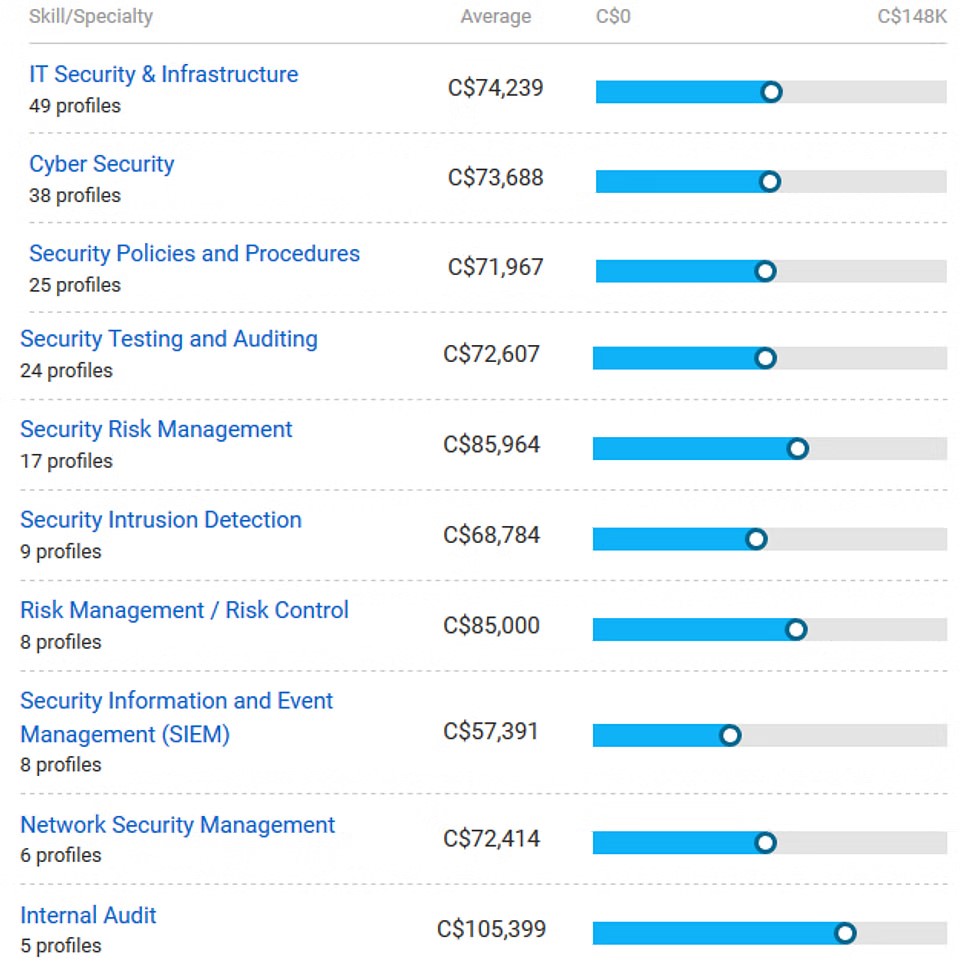
Image source: payscale.com
Companies that are hiring Certified Ethical Hackers:
- PricewaterhouseCoopers C$67,000
- RBC Bank C$69,490
- Rogers Communications Inc. C$70,829
Cities where Ethical Hackers are in demand:
- Toronto, Ontario C$50,147 – C$97,732
- Montréal, Québec C$51,500 – C$88,000
- Moncton, New Brunswick C$108,000
- Ottawa, Ontario C$70,000
- Vancouver, British Columbia C$84,000
Years of Experience:
- Less than 1 year 7%
- 1-4 years 36%
- 5-9 years 21%
- 10-19 years 27%
- 20 years or more 9%
Factors Influencing the Salary of Certified Ethical Hackers
- Expertise and Experience: Ethical hackers with extensive knowledge and a proven track record in cybersecurity often receive higher salaries.
- Industry: Certain sectors, such as finance and healthcare, prioritize security due to sensitive data concerns, leading to more competitive compensation packages for ethical hackers in these industries.
- Geographic Location: Salaries vary based on living costs, with higher pay typically found in cities compared to smaller towns or rural areas.
- Certifications: Credentials from reputable organizations like EC-Council or Offensive Security not only enhance skills but also increase an ethical hacker’s market value.
- Job Titles: Specialized roles like Penetration Tester or Security Analyst often command higher wages due to their specific nature and increased responsibilities.
Conclusion
The bottom line is that with the increasing rise in cybercrimes and threats severe tension across the globe is spreading like wildfire. If you’re someone who has a keen interest in cybersecurity or ethical hacking, a certified ethical hacker training program is all you need. As cybersecurity becomes an ever more critical concern in this era, organizations are recognizing the value of investing in top-notch ethical hackers, resulting in competitive compensation packages. The continuous evolution of cyber threats ensures that ethical hacking remains a pivotal and rewarding profession, attracting individuals with a passion for safeguarding digital landscapes against malicious activities.
