Table of Contents
ToggleCybercrimes and scammers, with the help of deep fake AI and advanced technologies, are vandalizing data security across the globe. From creating a fake AI image of Trump to looting the public by using gift-card scams, these kinds of cyber-attacks are becoming a terror of the current generation. Organizations are, therefore, focusing a lot on hiring certified Ethical Hackers to ensure absolute data security. With the latest technologies bringing tech revolution to the market, Ethical Hackers are rooting for the top seven Ethical Hacking tools in 2024.
What are Hacking Tools?
Ethical hackers use various software programs to perform various tasks, such as penetration testing, vulnerability assessment, security research, and cyberattacks. These are known as Hacking tools and can be classified into different categories, such as network tools, web application tools, wireless tools, password cracking tools, malware analysis tools, and more.
Hacking tools are not inherently illegal. They can be used for ethical hacking purposes, such as improving the security of systems and networks. However, some hacking tools can also be used for malicious or illegal purposes, such as stealing data, disrupting services, or compromising systems. Therefore, it is important to use hacking tools responsibly and legally.
What are the Benefits of Hacking Software?
Certified Ethical Hackers are in demand, and organizations are hiring them with lucrative salaries as data protection has become of utmost importance in every business. Thinking like a malicious hacker and, thereby, tracking how to protect confidential information is quite a big deal. Ethical Hackers use top-notch hacking tools or software to ensure no leaking of data, thus providing one hundred protection against cybercrimes. The following are the benefits of using hacking software:
- Comprehensive security measures to protect end users from internal and external threats.
- Network security testing to identify and address vulnerabilities.
- Utilization of ethical hacking software from open-source platforms for enhanced home network security.
- Option for vulnerability assessments to fortify networks or systems against external attacks.
- Application in auditing company security, ensuring smooth operation of computer systems without security issues.
Top Tools for Ethical Hacking
1. Nmap
One of the crucial phases of Ethical Hacking is Port Scanning and according to CEH, Nmap is the best hacking software for this phase. This command-line operating tool was developed to work on Linux or Unix, but now the Windows version is also available. Nmap is a versatile network security mapper, revealing services and hosts to create network maps. Its features include host discovery, operating system detection, and advanced vulnerability scanning. The software is script-extensible and adaptable to network conditions like congestion and latency.
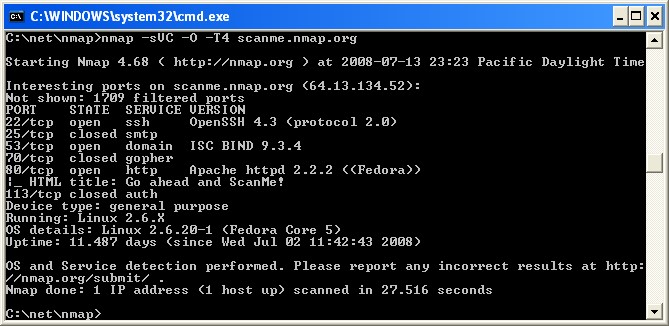
Image source: nmap.org
Nmap Hacking Tool Features:
- Used for auditing to identify target hosts.
- Identifies new servers.
- Queries a host for DNS and subdomain search.
- Finds vulnerabilities on a network and exploits them.
Nmap Hacking Tool Capabilities:
- Audits device security.
- Detects open ports on remote hosts.
- Performs network mapping and enumeration.
- Finds vulnerabilities within any network.
- Launches massive DNS queries against domains and subdomains.
Nmap Hacking Tool Price:
Free
2. Burp Suite
One of the greatest advantages of using Burp Suite as a hacking tool is that it helps speed up testing with the help of automated tools and workflows. You can customize your experience with Pro-specific BApps, a powerful API, and other user options.
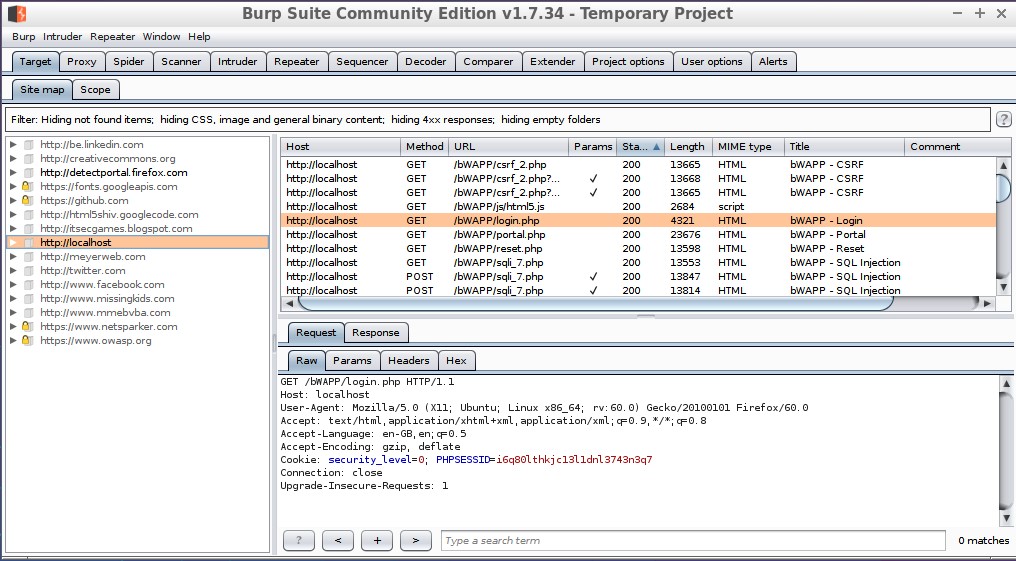
Image source: en.wikipedia.org
Burp Suite Hacking Tool Features:
- Allows editing of HTTP messages.
- Enables automated filtering of login sequences.
- Surveys weakness data with integrated vulnerability management.
- Automates scanning and filtering processes.
- Provides a wide array of technical and compliance reports effectively.
- Identifies critical vulnerabilities with 100% accuracy.
- Analyzes targets for vulnerabilities.
- Discovers content within the system.
- Facilitates task scheduling.
- Generates Cross-Site Request Forgery Proof of Concept.
Burp Suite Hacking Tool Price:
- Community edition: Free.
- Enterprise edition: Starts at $3999 per year.
- Professional edition: Starts at $399 per user per year.
3. Invicti
Invicti is a Proof-Based Scanning technology and security scanner hacking tool that helps SQL Injection, XSS, and vulnerabilities in web applications or services automatically and is mainly available for SAAS Solutions.
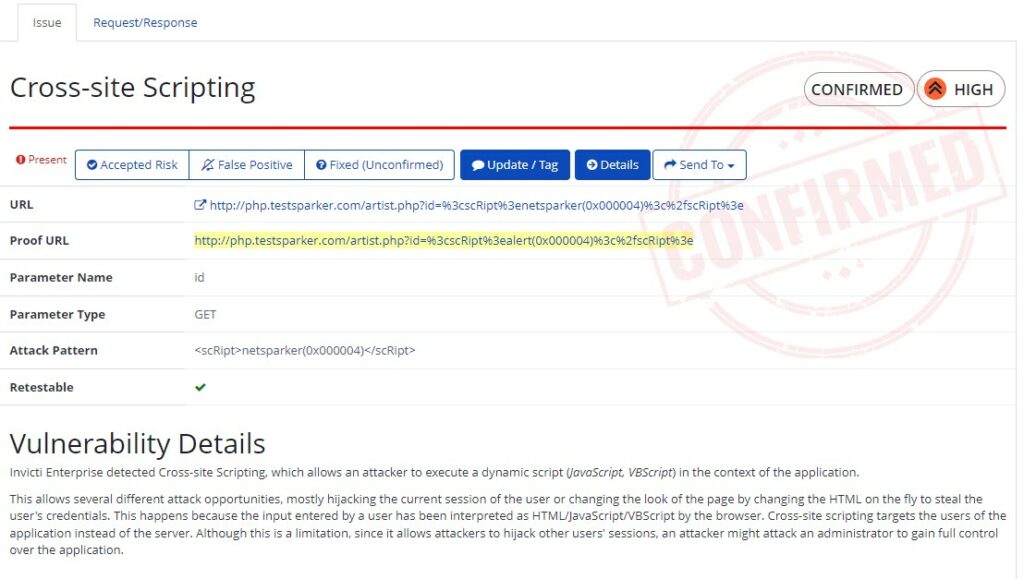
Image source: invicti.com
Invicti Hacking tools feature:
- Invicti’s Proof-Based Scanning boasts an accuracy rate of over 99.98%, as confirmed by the company’s security researchers analyzing the past five years of statistics.
- The research indicated that Invicti delivers precise automatic confirmation for 94.74% of detected direct-impact vulnerabilities.
- There’s no need for manual verification of identified vulnerabilities by the scanners, allowing you to save time in addressing and resolving them.
Invicti Hacking tools Price:
- Free Trial
- Premium- Price on request
- Enterprise- Price on request
4. Acunetix
Acunetix is a fully automated Ethical Hacking solution that scans single-page applications, javascript, etc., in just five steps. Acunetix automatically generates and maintains an updated list of your websites, applications, and APIs. This ensures that no potential entry points remain unscanned and vulnerable to attacks.
Image source: acunetix.com
Acunetix Key features:
- Conducts scans for various SQL Injection, XSS, and 4500+ vulnerabilities.
- Recognizes over 1200 vulnerabilities in WordPress core, themes, and plugins.
- Fast and scalable, capable of scanning thousands of pages without interruptions.
- Offered as both an On-Premises and Cloud solution.
- Seamless integration with popular WAFs and Issue Trackers to aid in the Software Development Life Cycle (SDLC).
Acunetix Price:
Free trial for 14 days

Image source: acunetix.com
5. Metasploit
Metasploit is the world’s most used penetration testing framework is a collaboration between the open source community and Rapid7. Metasploit enables security teams to go beyond merely confirming vulnerabilities, overseeing security assessments, and enhancing security awareness. It empowers defenders, arming them to consistently stay a step or two ahead in the game. A significant contribution of Metaspolit is that creates evasion and anti-forensic tools.
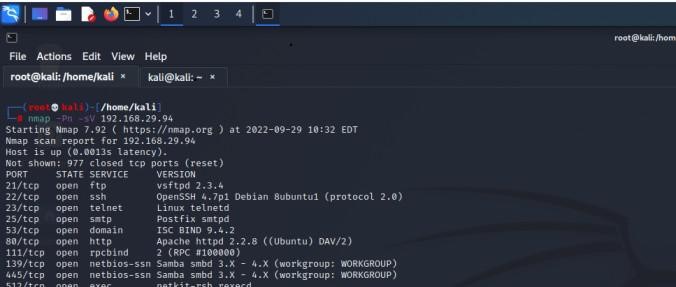
Image source: geeksforgeeks.org
Metasploit Key Features:
It serves to identify security vulnerabilities, aids in penetration testing and contributes to IDS signature development. Additionally, users can craft their security testing tools.
Metasploit Price:
- Open-source tool – Available for free download.
- Metasploit Pro is a commercial product with a 14-day free trial.
6. Ettercap
Ettercap is well known for its amazing Graphical User Interface (UI) and command line surface. Ettercap, an open-source tool, is employed for facilitating man-in-the-middle attacks on networks. It captures packets and subsequently reintroduces them into the network, allowing for the diversion and alteration of data virtually in real-time. Additionally, Ettercap serves for protocol analysis, which is essential in examining network traffic and also helps in creating plugins.
Image source: subscription.packtpub.com
Ettercap Key Features:
- Sniffing of live connections.
- Helps in content filtering.
- Allows active and passive dissection of many protocols.
- Facilitates network and host analysis.
- Allows creation of custom plugins using Ettercap’s API
Ettercap Price:
Free
7. Nessus
This hacking tool helps to fortify your web applications, gain visibility into your internet-connected attack surface, and secure your cloud infrastructure. Through collaborative community efforts and continual product innovation, Nessus delivers the most precise and comprehensive vulnerability data. This ensures that you don’t overlook critical issues that could pose a risk to your organization.

Image source: tenable.com
Nessus Key features:
- Nessus is versatile, deploying seamlessly on platforms like Raspberry Pi, ensuring full portability across diverse environments.
- Dynamic plug-ins boost scan efficiency for faster initial completion and quicker time-to-value.
- Conduct secure scans on web applications to pinpoint vulnerabilities within custom application code and third-party components precisely.
- Nessus helps you to secure cloud infrastructure before deployment and gain accurate visibility to the internet-facing attack surface.
Nessus Price:
Nessus Expert-
- 1 Year – $6,242.20*
- 2 Years – $12,172.29* (Save $312.11)
- 3 Years – $17,790.27* (Save $936.33)
Nessus Professional-
- 1 Year – $4,236.20*
- 2 Years – $8,260.59* (Save $211.81)
- 3 Years – $12,073.17* (Save $635.43)
Conclusion
This blog has discussed the top 7 Ethical Hacking Tools that will benefit Ethical Hackers and organizations in 2024. EC-Council Certified Ethical Hacker (CEH) Certification provides top-notch Ethical Hacking knowledge guidance to professionals who are looking for career advancement in Ethical Hacking. With technological advancement, scammers are also desperately looking for loopholes to attack organizations and demand ransomware. Ethical Hackers are betting on these Hacking Tools to eliminate most of the cyber attacks happening today.
