Table of Contents
ToggleIn the rapidly evolving world of software development, security has become a critical focus. However, traditional security practices often slow down the fast-paced delivery cycles that agile and DevOps methodologies offer. This is where DevSecOps comes into play.

DevSecOps integrates security practices into every phase of the DevOps process, ensuring that security is treated as a shared responsibility throughout the development lifecycle. The result is a more efficient, secure, and agile development process.
In this complete guide, we’ll explore the core concepts of DevSecOps, its benefits, challenges, best practices, and how it is revolutionizing the way organizations deliver secure software.
Understanding DevSecOps: The Basics
At its core, DevSecOps is about integrating security into the DevOps culture, automation, and processes. It shifts security to the left, meaning that security is no longer an afterthought but is incorporated from the very beginning of the development process.
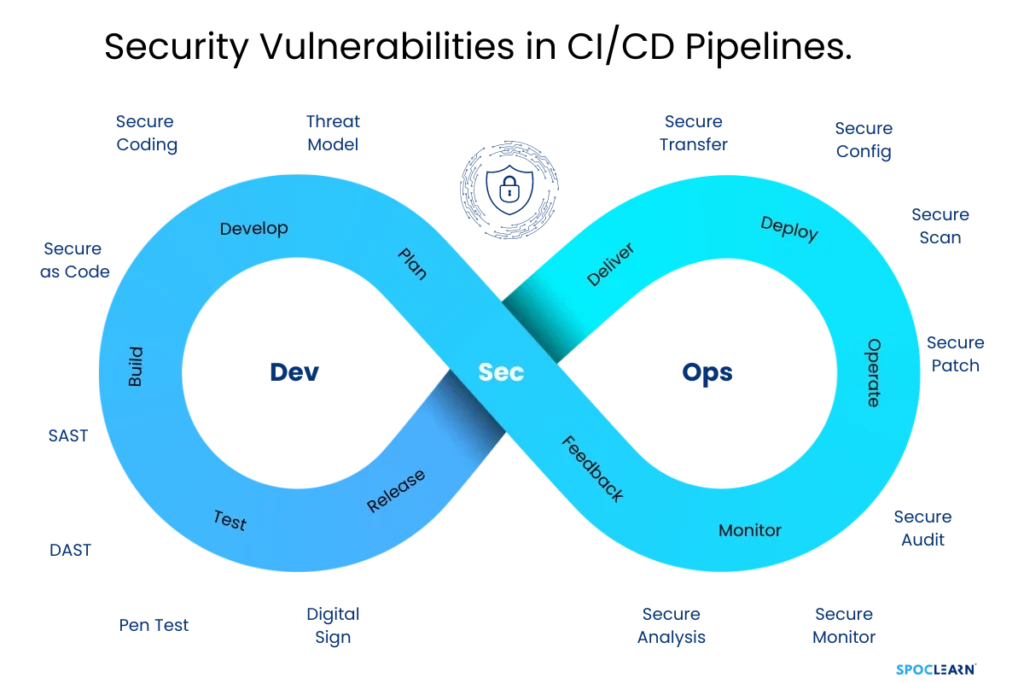
Traditionally, security would be implemented at the end of the software development lifecycle, often resulting in delays. With DevSecOps, security becomes everyone’s responsibility—from developers to IT operations and security teams.
By fostering collaboration between these groups, DevSecOps helps teams identify and address vulnerabilities early on. This integration ensures continuous security in the CI/CD (Continuous Integration/Continuous Delivery) pipeline.
The Need for DevSecOps in Modern Software Development
The increasing complexity of software systems, along with the growing threat landscape, necessitates the adoption of DevSecOps. According to industry reports, the number of cyberattacks continues to rise, with vulnerabilities often stemming from rushed development and insecure coding practices.
DevSecOps addresses this by embedding security from the start, which is crucial in today’s agile environments where software updates and features are pushed at an unprecedented rate.
Large enterprises like NCR and Aetna have already adopted DevSecOps practices to maintain security without slowing down their delivery cycles. By using automated security checks, organizations can detect and fix issues early, significantly reducing the risk of breaches.
Key Principles of DevSecOps
There are several fundamental principles that guide a successful DevSecOps strategy:
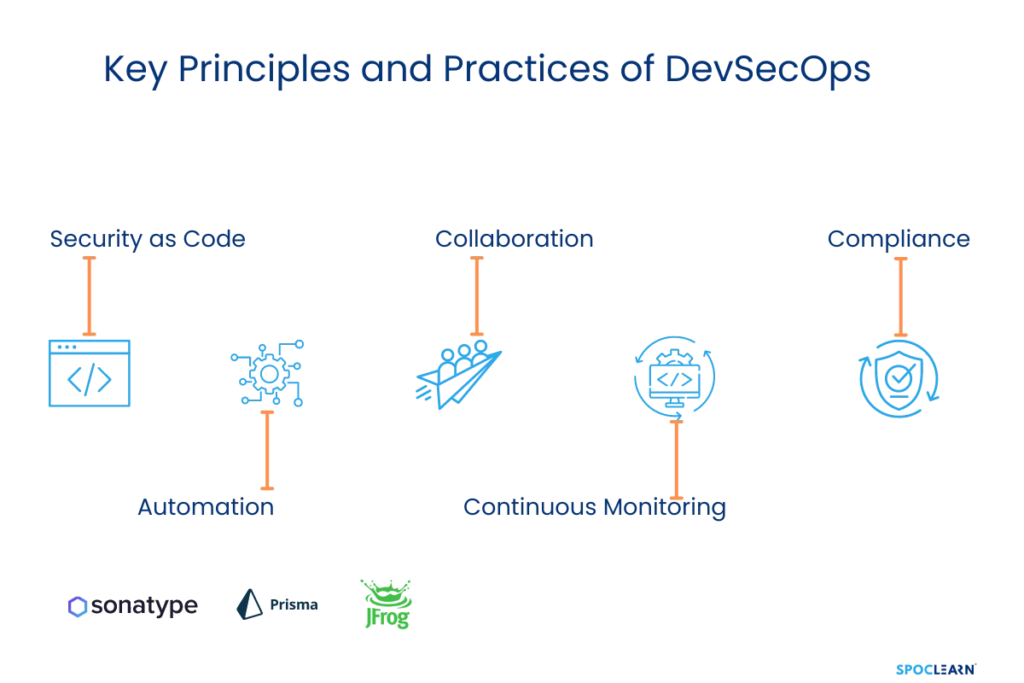
- Security as Code: Just as infrastructure is treated as code in DevOps, security in DevSecOps is automated and integrated directly into the development process.
- Automation: Automated tools for security testing, monitoring, and alerting are essential for ensuring continuous security in fast-moving DevOps environments.
- Collaboration: The security, development, and operations teams must collaborate throughout the software lifecycle. This includes shared responsibilities, tools, and goals.
- Continuous Monitoring: Security monitoring is ongoing, with real-time alerts to potential vulnerabilities or breaches, ensuring that issues are detected and dealt with promptly.
- Compliance: DevSecOps integrates automated compliance checks to ensure that software meets regulatory standards from the outset.
These principles are supported by the use of cutting-edge tools like Sonatype, JFrog, and Prisma, which enable continuous security in development and deployment.
Benefits of Implementing DevSecOps
DevSecOps offers numerous benefits to organizations that need to balance speed with security. Here are some of the key advantages:
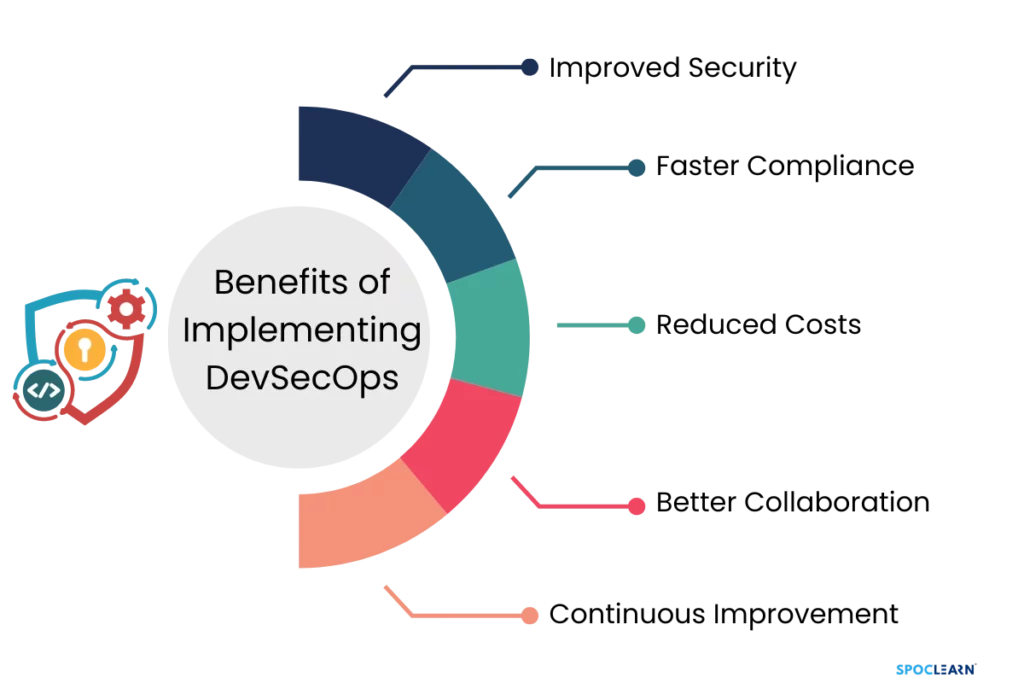
- Improved Security: By integrating security into every stage of the development process, vulnerabilities are detected and resolved early, reducing the risk of data breaches.
- Faster Compliance: Automated compliance checks ensure that the software complies with industry standards (e.g., GDPR, HIPAA) from the start, saving time during audits.
- Reduced Costs: Early detection of vulnerabilities reduces the cost associated with fixing security issues post-deployment.
- Better Collaboration: DevSecOps promotes a culture of collaboration between developers, security professionals, and operations teams, fostering a shared responsibility for security.
- Continuous Improvement: With continuous feedback loops, DevSecOps enables organizations to constantly improve their security practices based on real-time data and performance metrics.
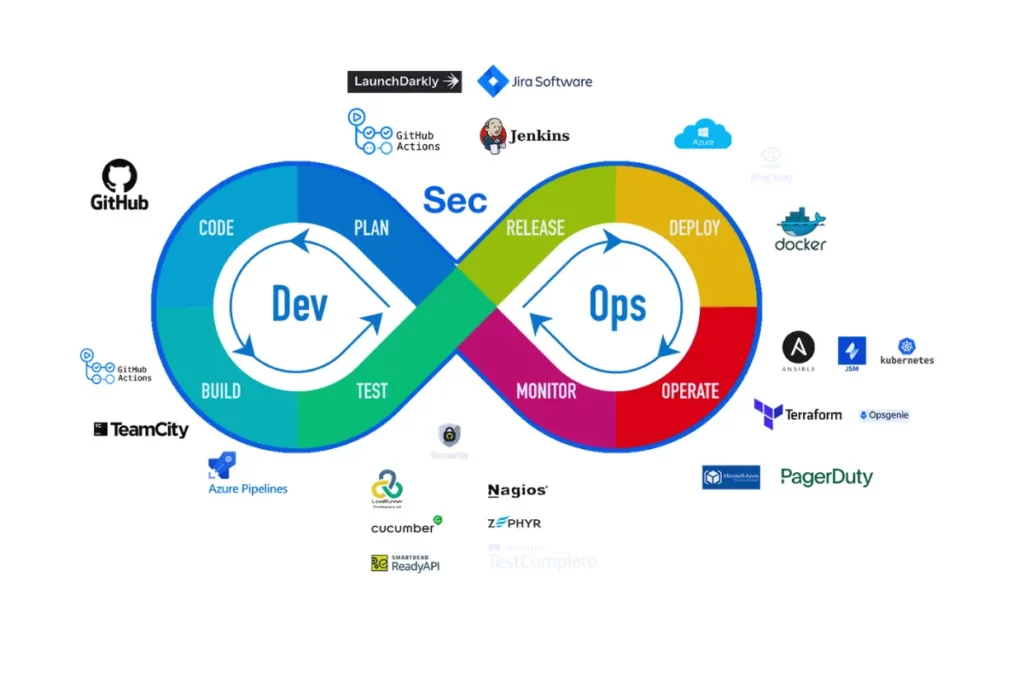
DevSecOps Workflow: How It Works
The DevSecOps workflow integrates security at every phase of the CI/CD pipeline. Here’s a breakdown of how it typically works:
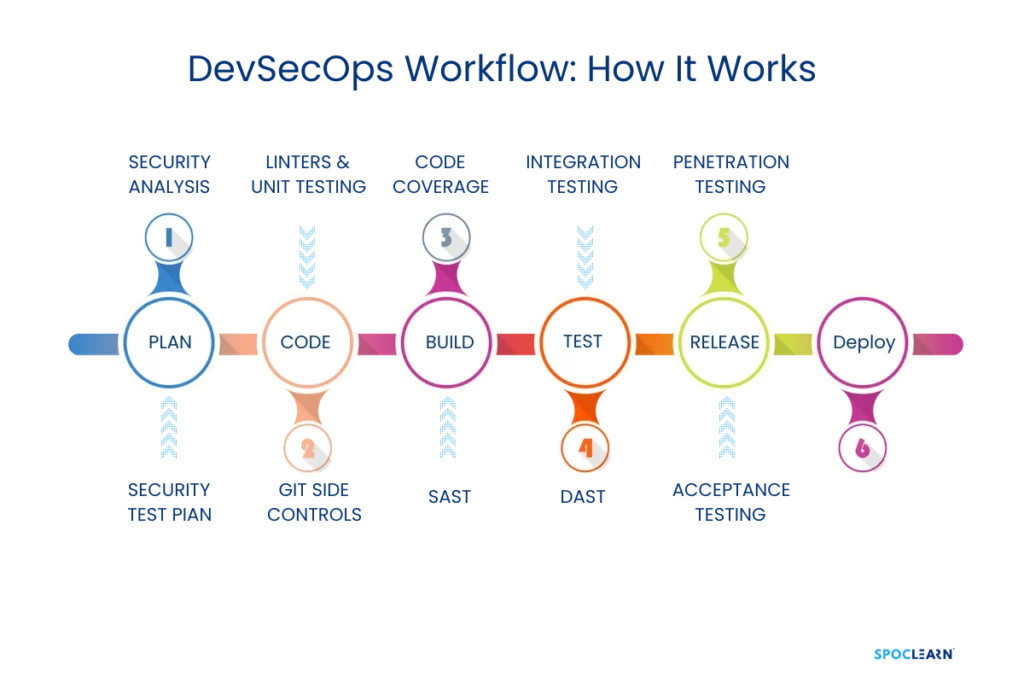
- Planning: Security considerations are part of the initial planning process. This includes identifying potential risks and regulatory requirements.
- Development: Secure coding practices are enforced, with automated static and dynamic security tests integrated into the development environment.
- Build: As the software is built, security vulnerabilities are automatically checked using tools like JFrog Xray.
- Testing: Continuous security testing is performed alongside traditional functional testing, ensuring that vulnerabilities are caught before deployment.
- Deployment: Security checks are conducted throughout the deployment process, with infrastructure-as-code policies ensuring secure configurations.
- Monitoring: Post-deployment, the software is continuously monitored for security threats and vulnerabilities using tools like Prisma Cloud.
Tools for DevSecOps
Several tools are essential for a successful DevSecOps implementation. These tools automate security checks, integrate with CI/CD pipelines, and provide real-time threat detection. Some of the most popular DevSecOps tools include:
- Sonatype Nexus: Ensures that components used in the software are free of vulnerabilities.
- JFrog Xray: A security tool that scans binary files to detect vulnerabilities.
- Prisma Cloud: Provides security for cloud-native applications, including container and Kubernetes security.
- Snyk: Focuses on identifying vulnerabilities in open-source dependencies.
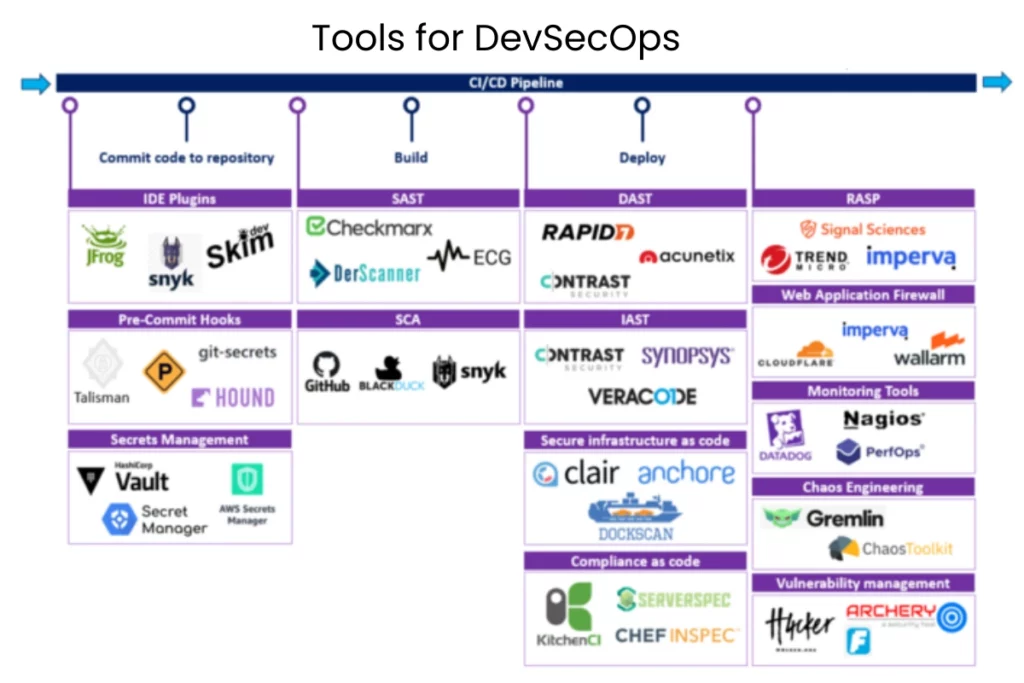
These tools, along with many others, automate the critical security tasks that allow DevSecOps teams to deliver software quickly and securely.
Challenges of Adopting DevSecOps
While DevSecOps offers numerous benefits, organizations often face challenges in its implementation:
- Cultural Resistance: Teams may resist changing their established workflows to integrate security practices.
- Lack of Expertise: Implementing DevSecOps requires skilled professionals who understand both development and security.
- Tool Complexity: With the variety of tools available, selecting the right one and integrating it into the existing pipeline can be challenging.

Despite these challenges, organizations like Maersk and Comcast have successfully overcome obstacles to implementing DevSecOps, showcasing the value of perseverance and proper planning.
Best Practices for Successful DevSecOps Implementation
To ensure a smooth DevSecOps transition, organizations should follow these best practices:
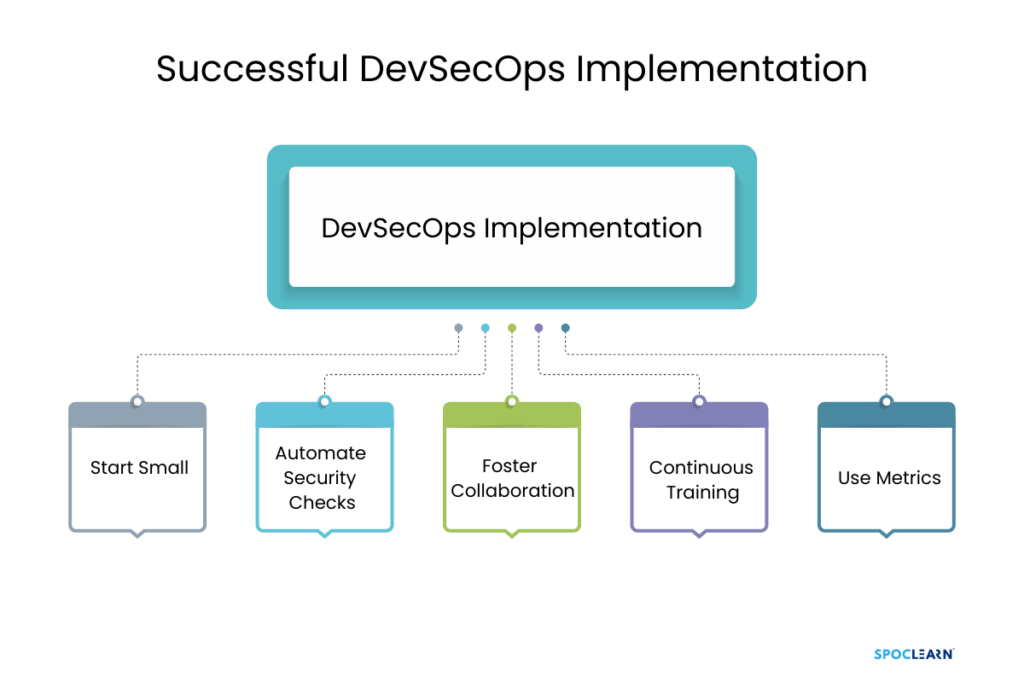
- Start Small: Begin by integrating security into one part of your pipeline and gradually expand across the development process.
- Automate Security Checks: Automation is key to success in DevSecOps. Implement tools that automate security tests and ensure continuous monitoring.
- Foster Collaboration: Encourage developers, security professionals, and operations teams to work together, sharing tools and goals.
- Continuous Training: Provide ongoing training to teams to ensure they stay updated on the latest security practices.
- Use Metrics: Continuously monitor security metrics and make adjustments based on data-driven insights.
Real-World DevSecOps Use Cases
DevSecOps has been successfully implemented by several organizations across industries:
- Aetna: The healthcare giant adopted DevSecOps to maintain application security across its platform.
- US Department of Defense: The DoD uses DevSecOps to ensure that security is integrated into its complex development processes.
- Maersk: Maersk adopted DevSecOps to secure its global logistics and supply chain operations.
These examples highlight the versatility and value of DevSecOps across different sectors.
The Future of DevSecOps
The future of DevSecOps looks promising, with trends pointing toward increased automation, AI-powered security tools, and more advanced monitoring capabilities. As cloud-native technologies and microservices become more prevalent, DevSecOps will play a crucial role in securing dynamic and distributed environments.
Expect to see tighter integrations between AI and DevSecOps tools, with predictive security models becoming a staple in the near future. Additionally, as regulatory requirements become stricter, organizations will increasingly rely on DevSecOps to maintain compliance in a fast-paced digital world.
Conclusion
DevSecOps represents the future of secure software development, blending speed, security, and collaboration. By integrating security at every stage of the software lifecycle, organizations can not only prevent breaches but also deliver faster, more reliable products.
As security threats evolve, DevSecOps provides a framework for continuous improvement, ensuring that security remains a priority without sacrificing agility.
© 2022 spoclearn.com