Table of Contents
ToggleEvery organization regularly performs a SWOT analysis where they evaluate the strengths and weaknesses along with looking for potential opportunities and threats. These threats can be external or internal depending on the current status of the businesses. Risk management is a crucial department in that every business invests a lot. Identifying risks and chalking out strategies to mitigate them is a fundamental responsibility and in this digital era, reportedly, online threats are petrifying the entire globe. The cybersecurity industry works with the utmost caution but given the current scenario, business analysts are also shaking hands with ethical hackers to protect businesses at all costs.

Why Business Analysts in Cybersecurity?
Since the pandemic has hit the market, cybercrime has increased quite high and the major reason is digital monetary transactions. Phishing emails, bank-related fake SMS, etc., are robbing people of their hard-earned money. Cybersecurity helps protect the organization’s data, systems, and sensitive information, often vital components of the projects people work on. Business Analysts (BA) may not be directly linked with implementing cybersecurity measures but their contribution is beyond comparison to maintaining an organization’s security posture.

Image source: actionfraud.police.uk
Business Analysts are well aware of the business position and can work on the threat model effectively. They deal with customers, stakeholders, project owners, clients, etc., and always track data related to these genres. Therefore, they can analyze what could be the potential organizational threats through predictive analytics and can take steps to stop any cyber attack.
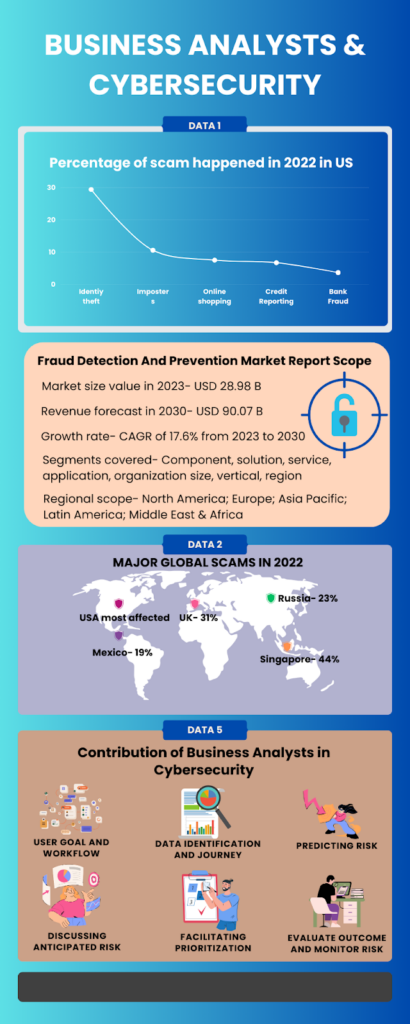
Roles of a Business Analyst in Cybersecurity
1. User Goal and Workflow
Business Analysts have to narrow down the risks and this step starts with understanding the user goals and workflows of the data. This in turn boosts analysis and leads conversations with the team. The stakeholders do not explicitly want to be involved with what the risks are, and they assume everything will be handled. Therefore, BA will have to be transparent about the scenario and explain whatever is happening or what could be the risks.
2. Comprehend the Trajectory of Data from Users to the Solution and Back to the Users
After gaining insight into the user’s workflow, you can delve into the journey of data. This involves identifying the data supplied by users and its traversal through various systems. This understanding will enable discussions about data that carries high risk, allowing you to concentrate efforts on safeguarding such data within the affected user workflows. Recognize that this is an ongoing and cyclical process.
3. Foresee Potential Areas of Risk
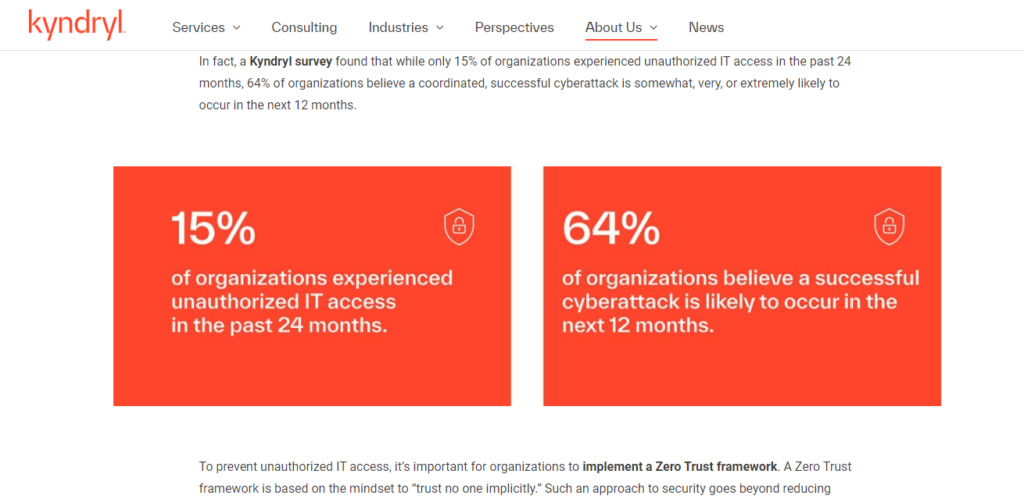
With user and data flow in sight, you can scrutinize and foresee where vulnerabilities may arise. These insights serve as the basis for initiating discussions with the team and stakeholders. Kyndryl survey provides this data that shows potential risks in cyber crimes or fraud detection in the upcoming years.
4. Facilitate Productive Discussions by Acting as a Bridge
Facilitating meaningful conversations involves introducing structure and encouraging participants to explore uncharted territory. Bring forward anticipated risks from the user’s perspective during discussions. Delve into potential risks, assess their magnitude, and encourage technical experts and business teams to collaborate on solutions. Act as the bridge, uniting everyone on a shared platform for meaningful discourse rather than engaging with each party separately.
5. Facilitating Prioritization
Assist stakeholders and teams in prioritizing non-functional security requirements based on business and user risk. Once the conversation is flowing, transition to facilitating prioritization. Acknowledge that achieving absolute security without any risk within budget and time constraints may not be feasible. Therefore, the focus should be on identifying what to secure first and considering different levels of security. You don’t need to be a cybersecurity expert, but as a facilitator, your role is to guide productive discussions and decisions, emphasizing user value and risk.
6. Evaluate and Monitor Outcomes and Risks
After implementation, the responsibility of the Business Analyst is to continually evaluate how the solution aligns with business needs and intentions. This applies to the realm of cybersecurity as well.
Future Trends in Cybersecurity
According to a Forbes article, here are some of the biggest cybersecurity trends that everyone should be ready for in 2024
1. The Cyber Security Skills Crunch
A shortage of professionals with the skills needed to protect organizations from cyber attacks continues to be a running theme throughout 2024. Efforts to rectify this situation will include a continued increase in salaries paid to those with the necessary skills, as well as greater investment in training, development, and upskilling programs.
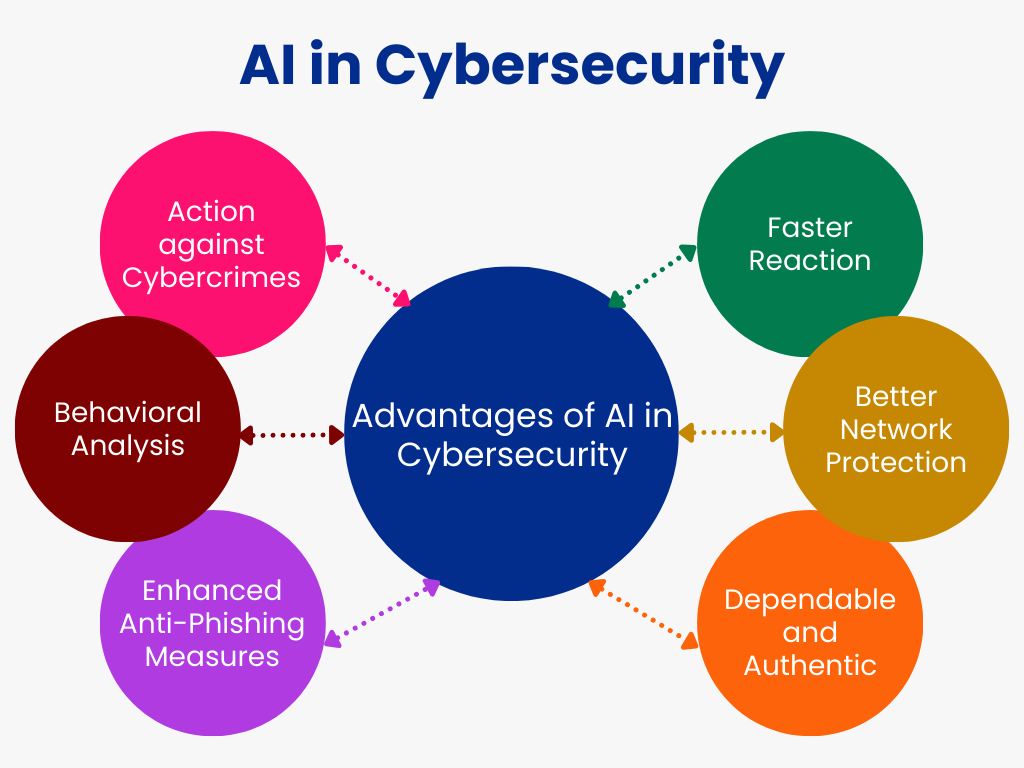
2. Generative AI Adopted on Both Sides of the Battle
As AI increases in sophistication, we will continue to see more sophisticated and smart AI-powered attacks. This will range from deepfake social engineering attempts to automated malware that intelligently adapts to evade detection. At the same time, it will help us detect, evade, or neutralize threats thanks to real-time anomaly detection, smart authentication, and automated incident response.
3. Next-Level Phishing Attacks
Phishing attacks are becoming more sophisticated and harder to detect. In 2024, we can expect to see more advanced phishing attacks that use AI and machine learning algorithms to create highly personalized and convincing messages.
4. IoT Cyber Attacks
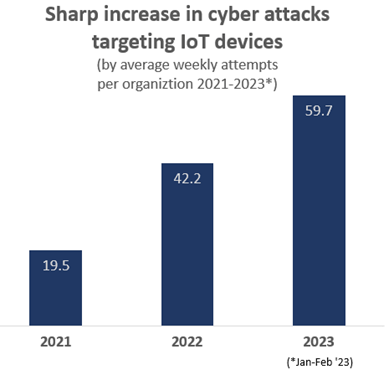
Image source: blog.checkpoint.com
With the global IoT-connected devices expected to surpass 75 billion by 2025, the massive proliferation of these devices symbolizes a significant security risk as they frequently lack robust built-in security.
5. Cyber Resilience – Beyond Cyber Security
Cyber resilience is the ability of an organization to prepare for, respond to, and recover from cyber-attacks. In 2024, we can expect organizations to focus more on cyber resilience rather than just cyber security.
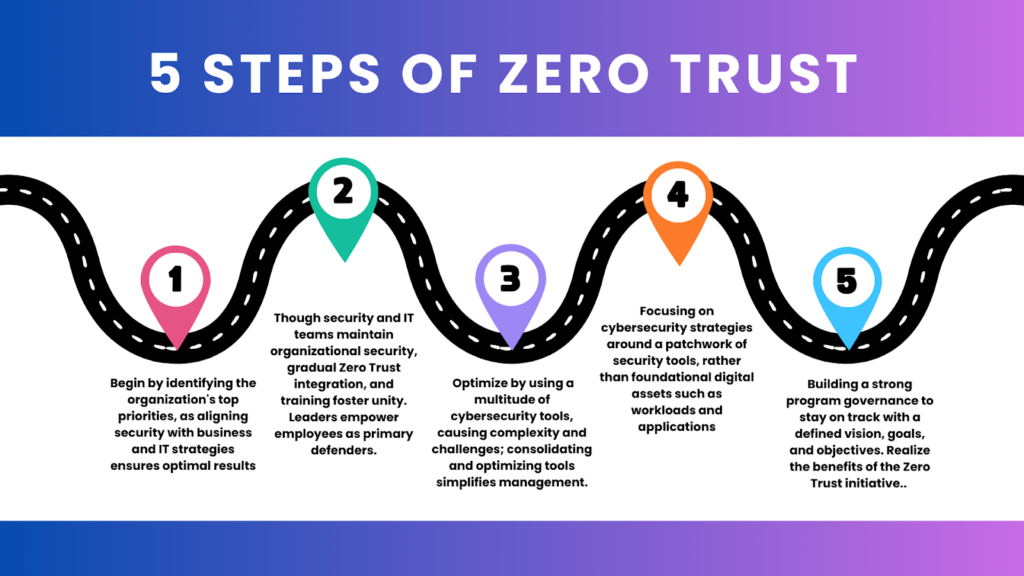
6. Less Than Zero Trust
Zero Trust is a security model that requires strict identity verification for every user or device trying to access resources on a private network regardless of whether they are inside or outside the network perimeter.
7. Cyber Warfare and State-Sponsored Cyber Attacks
Nation-state actors will continue to use cyber attacks as a tool for espionage, sabotage, and political influence in 2024.
BA Keeping Up with the Latest Cybersecurity Roles

1. Risk Assessment and Prioritization
Conducting risk assessments helps identify potential vulnerabilities and threats that the organization faces. By working closely with stakeholders to prioritize these risks, business analysts can direct resources and efforts toward the most critical security areas.
2. User-Centric Approach
In today’s user-driven world, security measures must be balanced with user experience. Business analysts play a vital role in ensuring that security solutions don’t hinder user productivity or satisfaction. Finding the right balance is key to successful security implementation.

3. Security by Design
Building security into projects from the outset is more effective than retrofitting it later. Business analysts should advocate for a “security by design” approach, emphasizing that security considerations be part of the initial project planning and design stages.
4. Data Protection and Privacy Compliance
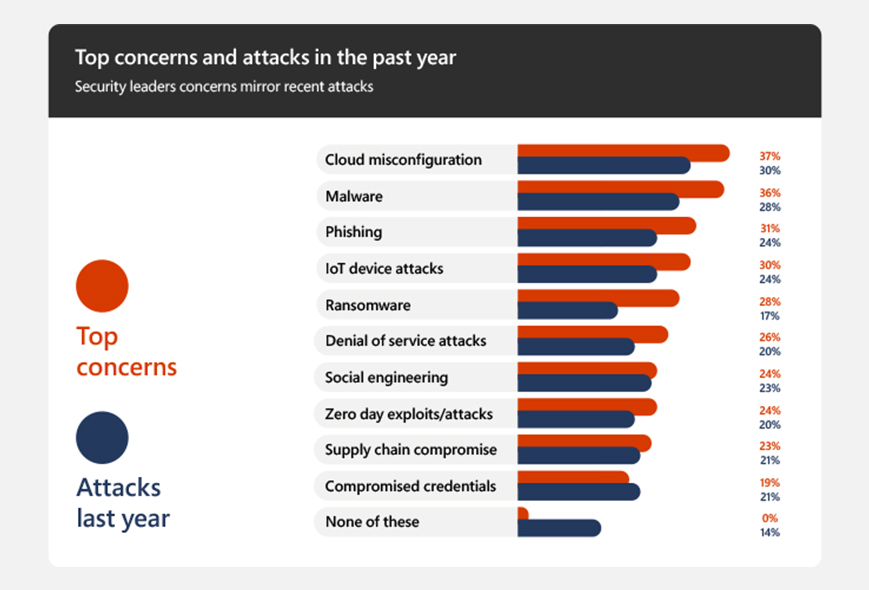
Data protection and privacy are increasingly important as data breaches and regulations become more stringent. Business analysts must ensure that the organization’s data handling practices comply with relevant laws and standards, safeguarding sensitive information. Microsoft came up with this data in 2022 that showed the top cyber crime attacks and the areas of concern in 2021
5. Incident Response Planning
Security incidents are almost inevitable, so being prepared is essential. Business analysts should work with stakeholders to create detailed incident response plans. Understanding the potential impact of these incidents on the business allows for the development of effective response strategies to minimize damage and downtime.
Conclusion
Cybersecurity, therefore, is not just about ethical hackers dealing with malicious ransomware attacks. BA professionals are also working on similar issues and utilizing their analytical skills to predict any possible threats. They communicate with stakeholders and other required members about any risks. The need for Business Analysts in cyber security has been piqued mainly due to the increase in cyber crimes and the dire need for predicting any risk. With artificial intelligence and major analytical tools, BA is contributing massively to the field of cyber security.
