Table of Contents
ToggleVulnerability management as the name suggests is a process where risks or vulnerabilities are detected in web applications, computers, mobile devices, and software. The process includes identifying, prioritizing, and mitigating security risks throughout the IT environment regularly. With the increasing level of cyber attacks, ransomware, deepfake AI, etc., organizations are facing severe cyber threats and hence, professionals expert in Vulnerability Management, especially in cybersecurity, are in great demand. Let’s discuss the importance of Vulnerability Management and how it is being taken care of.

Vulnerability Management: Definition

The function of vulnerability management entails proactively seeking out, identifying, and mitigating all vulnerabilities within an organization’s IT infrastructure before they are exploited by malicious actors. These vulnerabilities may exist in hardware devices, endpoints, software applications, and the overarching network structure. Common vulnerabilities include weak passwords, outdated software, unpatched systems, and misconfigured networks.
Typically, numerous vulnerabilities coexist within a company’s IT landscape at any given time. A key component of the vulnerability management process involves not only detecting vulnerabilities but also prioritizing and addressing them based on their severity. While vulnerability assessment entails identifying and evaluating potential weaknesses within a network, vulnerability management focuses on mitigating or eliminating these weaknesses.
Case Study: Vulnerability Management at Tulane University
Source: www.digitaldefense.com
Tulane University, a higher education institution, faced unique cybersecurity challenges. With more than 16,000 students, faculty, and staff, the university had to ensure the security of its network while also allowing access to necessary data for projects and research.

Image source: www.usnews.com
The Challenge
The university’s network was accessed multiple times a day through various endpoints such as laptops, phones, and other personal devices. This potentially opened doors for cyber-criminals who can easily access sensitive data which left the university vulnerable to a devastating breach.
The Solution
To manage ongoing threats and meet data protection requirements, Tulane turned to Digital Defense for a vulnerability management solution. They leveraged DD’s Frontline Vulnerability Manager (Frontline VM), which effectively identified internal and external vulnerabilities that could be exploited by cyber-criminals.
The Outcome
With Frontline VM, Tulane streamlined processes and improved data security. The solution provided actionable reports, unlike their previous network scanning tool, which provided large amounts of static and extraneous data. The university found Frontline VM to be advanced, intuitive, and cost-effective.
This case study demonstrates the importance of a strong vulnerability management program in protecting an organization’s network and data. It also highlights the role of effective tools in identifying and managing vulnerabilities.
Vulnerability Management Lifecycle
The lifecycle process may vary across companies, tailored to individual needs and requirements. However, in most instances, it generally follows a five-step model. This framework ensures that your vulnerability management lifecycle yields effective results by addressing even the most obscure security vulnerabilities.
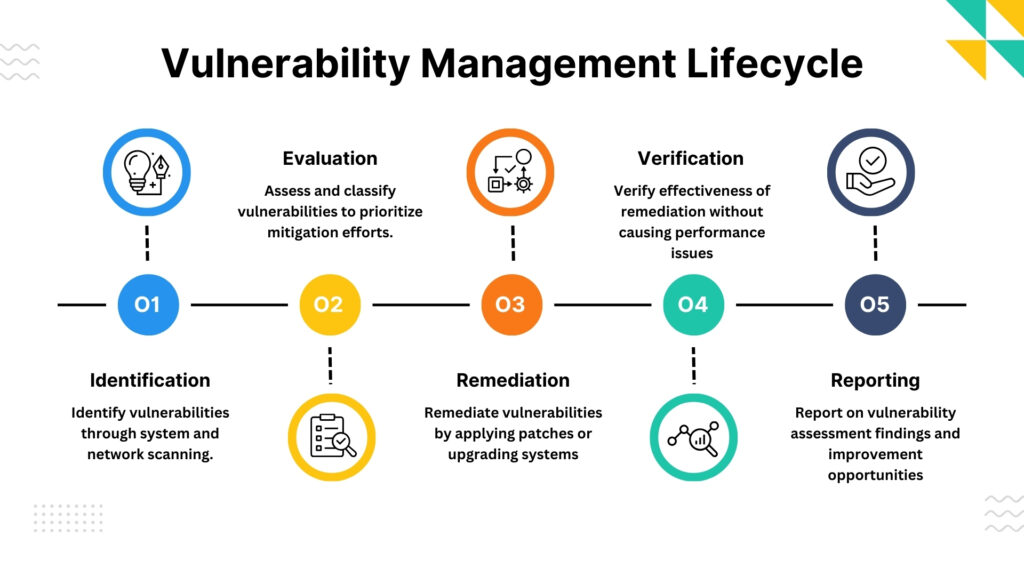
Identification
This initial phase involves scanning systems and networks to detect potential vulnerabilities. Organizations use this phase to uncover and document vulnerabilities within their systems, either through manual inspection or automated scanning utilizing network-based or agent-based vulnerability scanner tools.
Evaluation/Classification
Following the identification of vulnerabilities, they undergo an assessment to determine their severity and associated risks. This information is crucial for prioritizing which vulnerabilities should be addressed first.
Remediation
Once prioritized, remediation efforts commence, typically involving software patching or system upgrades. This may also entail implementing workarounds or mitigations. It is imperative to test these fixes in a controlled environment before widespread deployment, as patches can sometimes introduce functional issues, leading to system downtime and potentially providing opportunities for cybercriminal exploitation.
Verification
It is essential to verify the effectiveness of remediation and mitigation steps while ensuring that the changes do not adversely affect device performance, thus avoiding downtime. This phase also presents an opportunity to identify best practices and areas for process improvement in the future.
Reporting
In today’s competitive business landscape, delivering top-notch IT services is not sufficient; demonstrating the value of your efforts through consistent reporting is equally important. The vulnerability assessment and management report should outline the number of vulnerabilities identified and remediated, the assessment and remediation process, its scope, and any enhancements made. This report should provide actionable intelligence to enhance future processes.
Why do Organizations Need Vulnerability Management?
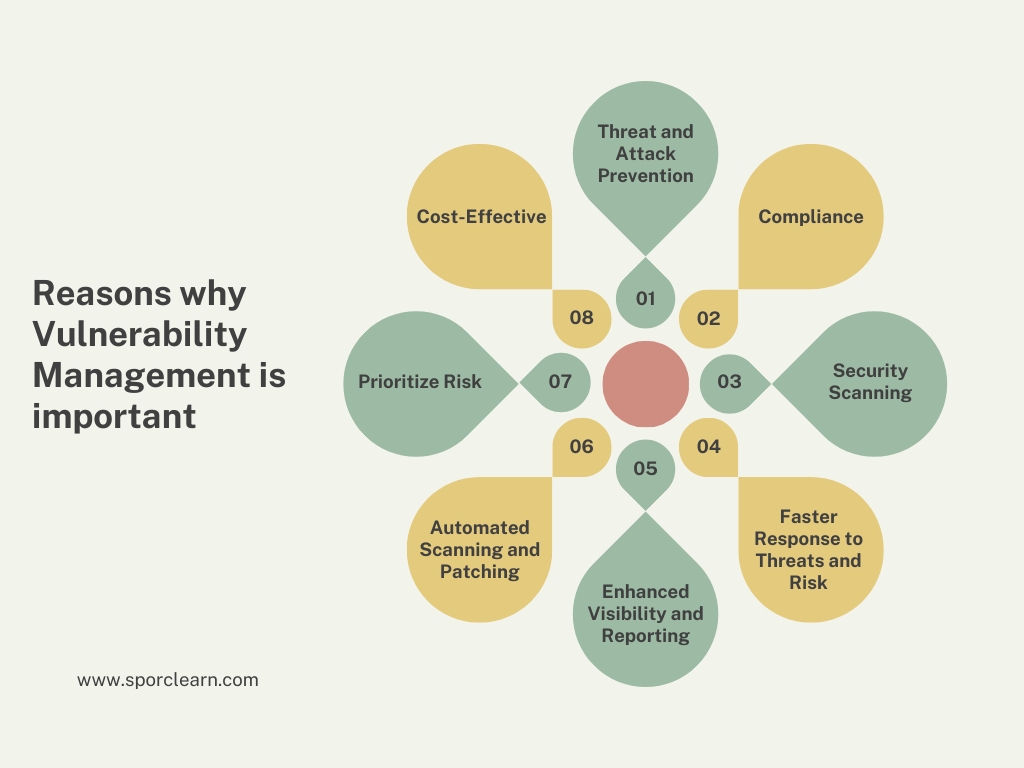
- Threat and Attack Prevention: Vulnerability management helps organizations identify potential weaknesses in their systems which can be exploited by cybercriminals. By proactively identifying these vulnerabilities, organizations can prevent potential cyber-attacks, thereby protecting their systems and data.
- Compliance: Critical industry sectors, such as healthcare and finance, have regulations that require companies to manage vulnerabilities effectively. Failure to comply with these regulations can result in penalties, including fines and reputational damage.
- Security Scanning: Regular security scanning is a key component of vulnerability management. These scans help identify new vulnerabilities that may have been introduced through software updates, new installations, or changes in the IT environment.
- Faster Response to Threats and Risk: With a proper vulnerability management process in place, organizations can respond to threats more quickly. This is because they are aware of their vulnerabilities and can take immediate action to address them, thereby reducing the potential damage.
- Enhanced Visibility and Reporting: Vulnerability management provides visibility into the security posture of an organization. This includes information about the number and severity of vulnerabilities, the effectiveness of remediation efforts, and the overall risk level. This information can inform decision-making and demonstrate compliance with industry regulations.
- Automated Scanning and Patching: Automation can make the process of finding and fixing vulnerabilities more efficient. Automated tools can scan for vulnerabilities, prioritize them based on risk, and apply patches or other remediation measures. This not only saves time but also reduces the likelihood of human error.
- Prioritize Risk: Not all vulnerabilities present the same level of risk. Some may pose a significant threat to the organization, while others may be less critical. Vulnerability management helps organizations prioritize their remediation efforts based on the risk each vulnerability presents.
- Cost-Effective: Proactively managing vulnerabilities can be far less costly than responding to a security breach after it has occurred. The costs associated with a breach can include financial losses, damage to the organization’s reputation, and loss of customer trust.
Top 5 Challenges in Vulnerability Management
- Incomplete asset inventory poses challenges due to difficulties in maintaining an up-to-date register of digital assets like the CMDB, leading to incomplete visibility of the attack surface.
- The overwhelming scope of vulnerabilities is evidenced by the staggering number identified in scans, creating an unmanageable backlog for vulnerability management teams.
- Prioritizing vulnerabilities is complex, as generic scoring systems like CVSS may not accurately reflect the risk to an organization, resulting in critical vulnerabilities being overlooked.
- Manual processes and lack of automation in vulnerability management lead to inefficiencies, slow patching, and increased likelihood of errors.
- Monitoring and reporting vulnerabilities manually is labor-intensive and prone to gaps, limiting visibility into past and present remediation activities and vulnerability risk.
- Lack of human resources exacerbates the challenges of vulnerability management, with teams struggling to keep up with workload demands and manual processes.
To enhance vulnerability management, teams require
- An accurate asset inventory for complete visibility.
- Fast, intelligence-led prioritization of vulnerabilities.
- Continuous monitoring of processes and outcomes.
- Comprehensive automation and orchestration support.
Conclusion
Effective vulnerability management is critical for organizations to mitigate cybersecurity risks and protect business-critical assets from exploitation. By maintaining accurate asset inventories, prioritizing vulnerabilities intelligently, implementing automation and orchestration, and continuously monitoring and reporting on the vulnerability landscape, teams can reduce the likelihood of breaches and minimize their impact. Investing in robust vulnerability management practices not only strengthens cybersecurity defenses but also helps organizations maintain regulatory compliance and safeguard their reputation in an increasingly hostile digital landscape. Spoclearn’s CISM Certification training and CRISC certification training extensively cover the topic of vulnerability management and its importance in today’s evolving business landscape.
