Table of Contents
ToggleAre you a cybersecurity enthusiast confused about choosing the ideal certification for your career growth? Two major cybersecurity certifications CISA and CISM provided by ISACA (Information Systems Audit and Control Association) are the most sought-after certifications for professionals choosing a strong cybersecurity path. Technology has evolved a lot and with never-ending cyber threats, organizations are looking for CISA-certified audit professionals, and CISM-certified in information security management. This blog will cater to straightforward decisions between CISA and CISM that will help you choose the one that suits you the best.
CISA vs CISM: What are the differences?
Both the Certified Information Systems Auditor (CISA) and Certified Information Security Manager (CISM) certifications offer unique viewpoints and abilities, making them valuable for people aiming to succeed in various areas of Information Security and management.
CISA focuses on checking and managing information systems to ensure they’re safe and risks are handled properly. The CISA exam includes topics such as auditing information systems, managing IT governance, acquiring and developing information systems, maintaining and managing information systems, and safeguarding information assets. CISA holders need to complete annual professional education to keep their certification active.
Read: What is CISA Certification?
On the other hand, CISM concentrates on creating and overseeing information security programs. Like CISA, CISM is managed by ISACA and requires passing an exam covering information security governance, risk management, developing and managing security programs, and handling security incidents. Continuous education is also necessary to maintain an active CISM certification.
The table below will help you understand the ground differences between CISM and CISA:
| Parameters | CISA | CISM |
| Target | Auditing and controlling information systems | Establishing and managing information security programs |
| Governing Body | ISACA | ISACA |
| Exam Content | IT auditors Compliance professional risk managers | Information security management governance |
| Prerequisites | Single exam 5 years of experience auditing, controlling, monitoring, and assessing IT systems preferred | Single exam, 5 years of professional information security experience preferred |
| Renewal | 120 credits over 3 years | 121 credits over 3 years |
| Career Path | IT auditCybersecurityCompliance | IT auditorsCompliance professional risk managers |
| Skills Required | Auditing, risk management, controls, audit frameworks, and standards | Security program management, governance, risk management, leadership |
| Overlap | Moderate overlap in knowledge areas | Low overlap between focus areas |
| Ideal Candidate | IT auditorsCompliance professionalsRisk managers | Information security managers CISOs Security program leaders |
Certification Domain: CISA vs CISM
ISACA has defined five critical CISA domains that you will be tested on:
- Domain 1 – Information System Auditing Process- 18%
- Domain 2 – Governance and Management of IT- 18%
- Domain 3 – Information Systems Acquisition, Development, and Implementation- 12%
- Domain 4 – Information Systems Operations and Business Resilience- 26%
- Domain 5 – Protection of Information Assets- 26%
Source: ISACA CISA Exam Outline
ISACA has defined four critical CISM domains that you will be tested on:
The four domains are:
- Domain 1– Information Security Governance- 17%
- Domain 2– Information Risk Management- 20%
- Domain 3– Information Security Program Development and Management- 33%
- Domain 4– Information Security Incident Management- 30%
Source: ISACA CISM Exam Outline
CISM vs CISA- Target Audience
Anyone interested in IS auditing, control, or security can take the CISA exam. It lasts for four hours and consists of 150 multiple-choice questions divided into five areas: Auditing of Information Systems, Process IT Governance, and Management. Following is the target audience for a CISA certification:
- IS/IT Auditors/Consultants
- IT Compliance Managers
- Chief Compliance Officers
- Chief Risk & Privacy Officers
- Security Heads/Directors
- Security Managers/Architects
- Required for everyone who manages, monitors, or evaluates an organization’s information technology and business systems
- Individuals who may wish to become CISA-certified
In the realm of information security, having a CISM certification is highly regarded. The ideal candidates for this certification include security consultants and managers, IT directors, etc.
- IT Professionals
- Cybersecurity Experts
- IT Auditors
- Risk Managers
- Compliance Officers
- Security Consultants
- CISM is ideal for professionals with experience in managing, designing, overseeing, and assessing an enterprise’s information security program
- Professionals to boost information security management careers and broaden their knowledge of global security practices
Prerequisites and Exam Format For CISA and CISM Certification
For CISA Certification
ISACA, the organization behind the CISA, states that those interested in information systems auditing, control, and security can obtain the certification if they fulfill the following requirements:
- Pass the CISA certification exam.
- Acquire the necessary job experience.
- Complete a CISA certification application.
It’s not necessary to meet the experience criteria before passing the CISA exam.
However, regardless of the order in which you complete these steps, you must pass the exam and gain job experience before receiving the CISA certification.
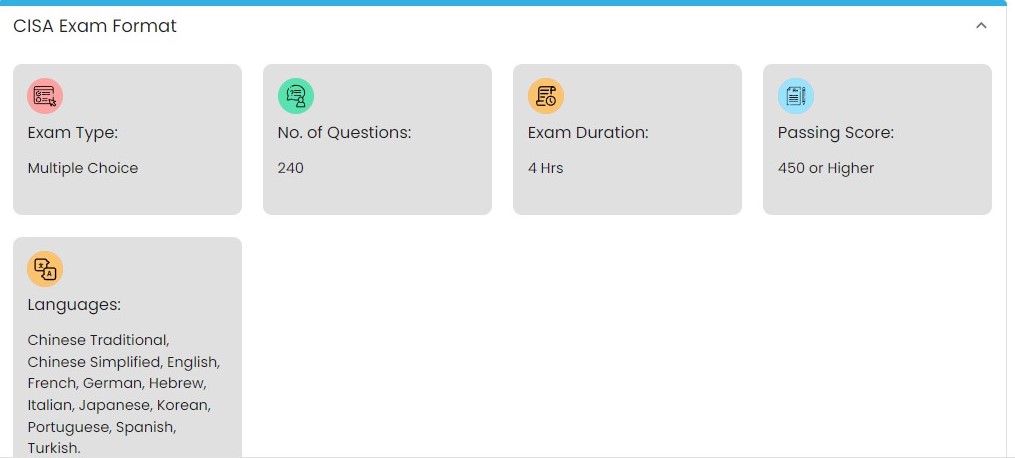
Image source: www.spoclearn.com
After obtaining your CISA certification, you must maintain it by
- Adhering to the ISACA Code of Professional Ethics.
- Meeting the requirements of Continuing Professional Education programs.
- Complying with Information Systems Auditing Standards during audits.
The standards for CISA certification aren’t overly complex, but achieving them requires time, effort, and financial investment, similar to any qualification. Understanding each requirement can help you assess if the commitment is worthwhile.
For the CISM certification
Candidates must adhere to ISACA’s Code of Professional Ethics and have five years of experience in the information security field. This work experience must be gained within ten years before the certification application deadline or within five years after passing the first exam. Specifically, three of the five years of experience must have been in an information security manager role.
The CISM exam is offered twice a year, in June and December. It’s a four-hour exam comprising 150 multiple-choice questions covering four areas of information security.
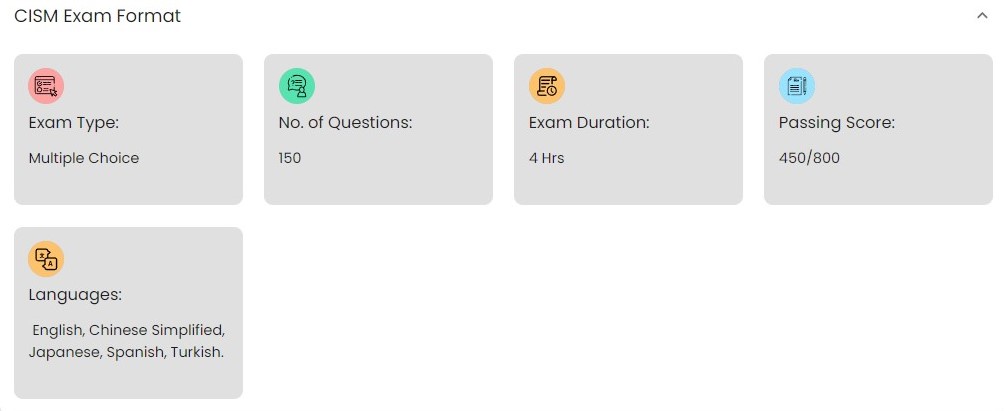
Image source: www.spoclearn.com
Job Opportunities for CISA-Certified Professionals
Professionals who earn the Certified Information Systems Auditor (CISA) certification often take on roles that heavily focus on auditing and assessing the security of information systems. Their typical job duties include:
- Conducting thorough audits of policies, procedures, operations, and technical controls to identify risks, ensure compliance, and suggest protective measures.
- Delving into details by testing systems, analyzing data, and documenting audit findings.
- Assessing both new and existing systems to offer insights on incorporating proper security measures.
- Reviewing existing information systems and advising on security measures during the development and implementation of new systems.
- Evaluating IT infrastructure and applications to identify vulnerabilities, gaps, and compliance issues.
- Developing and executing audit plans based on risk factors specific to the organization’s environment and industry regulations.
- Presenting audit findings to management and proposing recommendations to enhance security measures and address compliance gaps.
- Monitoring the resolution of issues and validating solutions that strengthen security and address weaknesses in controls.
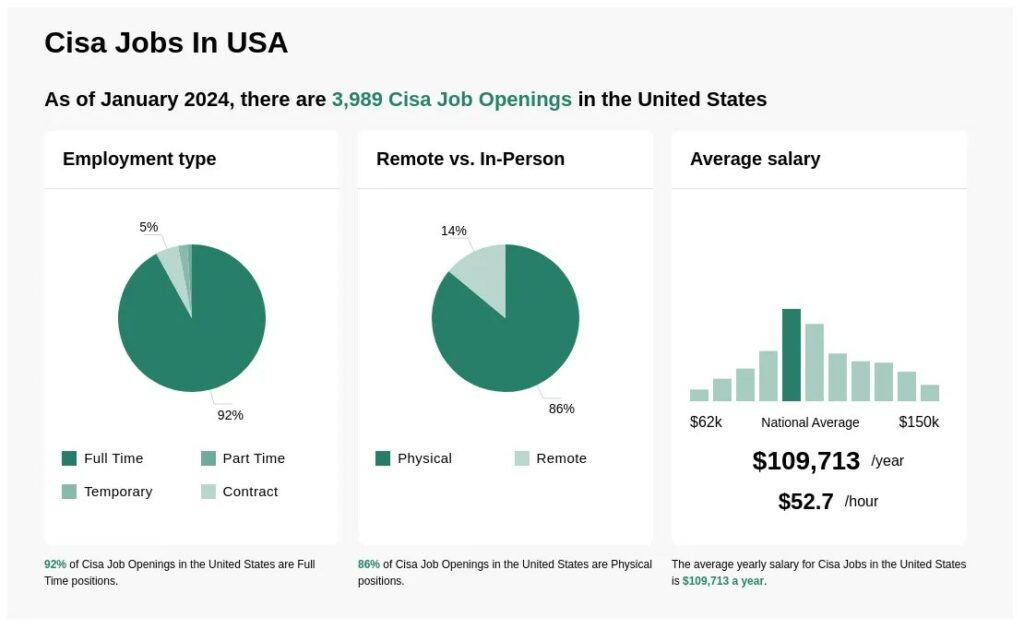
Image source: www.ziprecruiter.in
Skills required for cracking a CISA job are
- A deep understanding of information systems infrastructure, applications, operations, and security controls, along with the capability to delve into technical intricacies.
- Familiarity with IT governance, frameworks, controls, and auditing standards.
- Competence in risk assessment, data analysis, and research to identify vulnerabilities and compliance shortcomings.
- The ability to grasp and interpret regulations and translate them into auditing procedures.
- Excellent communication skills to convey findings and recommendations effectively.
- Proficiency in audit techniques such as evidence gathering, interviewing, control testing, and result documentation.
- Analytical thinking and attention to detail when evaluating audit evidence and identifying root causes.
CISA Salary Structure
CISA certification is popular now, with over 151,000 experts already certified by ISACA by 2022. If you have this certification, you can earn a good salary. Skillsoft data from October 5, 2022, says that it’s one of the top 15 highest-paying IT certifications of the year. On average, people with CISA certification make about $142,336.58 a year, which is 5% more than in 2021.
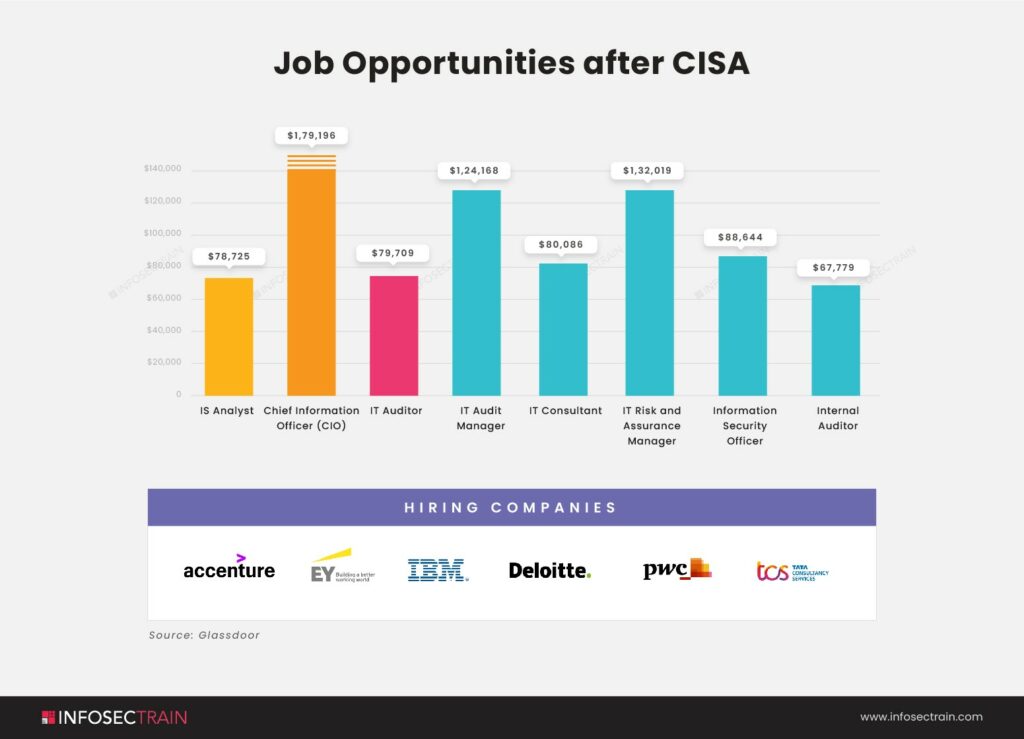
Image source: www.infosectrain.com
A report by the Institute of Internal Auditors (IAA) found that people with a CISA certification make a lot more money than those without it. On average, CISA-certified people earn around $105,000, while those without it make about $65,000.
Where you work and what position you have can really affect how much you earn with a CISA certification. People working in big cities and developed countries usually make more than those in developing countries.
If you’re just starting with CISA, you might make around $60,000 a year, but experienced professionals in high-level positions can earn up to $175,000 annually. That’s more than a 50% difference! Even between entry-level and junior-level positions, there’s a big gap – entry-level positions usually pay about $75,000.
Your salary can also depend on the size of the company you work for. In medium-sized companies, entry-level positions might pay around $57,000, while in larger companies, it could be closer to $63,000. That’s about an 8% difference.
Different career paths within CISA can also lead to different salaries. For example, senior information technology auditors make around $88,933 a year, while chief information security officers can earn up to $183,467 annually. So, where you work, what position you have, and your career path all play a big role in how much you earn with a CISA certification.
Job Opportunities for CISM-Certified Professionals
People with a CISM certification lead security programs, create strategies, oversee teams, advise management, and handle incidents to protect information assets and infrastructure effectively. The job responsibilities of a CISM-certified professional are
Leadership roles: Pursuing CISM certification often leads to leadership positions in managing comprehensive security programs.
Responsibilities:
- Develop information security strategies, policies, standards, procedures, and metrics in line with business objectives.
- Oversee and govern the end-to-end security program to protect information assets and technology infrastructure.
- Manage teams responsible for operations, incident response, risk assessment, and other security aspects.
- Advise executive management and collaborate with other leaders on security initiatives and investments.
- Coordinate activities across departments and teams to ensure consistent enforcement of policies and maintenance of protections enterprise-wide.
Incident Management:
- Lead investigations, forensic analysis, and remediation when security incidents occur.
- Report on the effectiveness of the security program and identify areas for improvement.
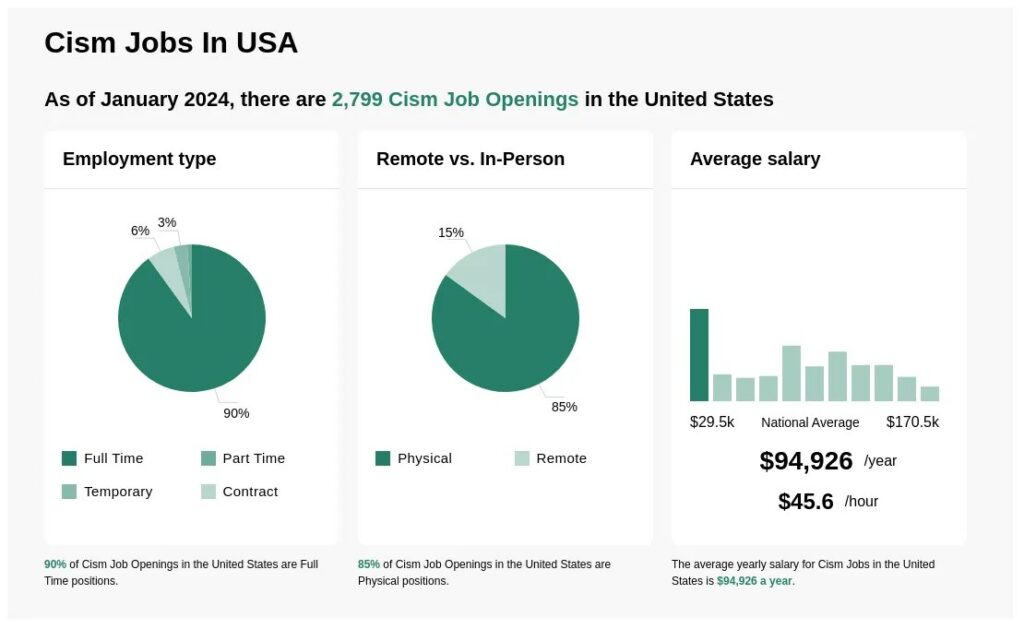
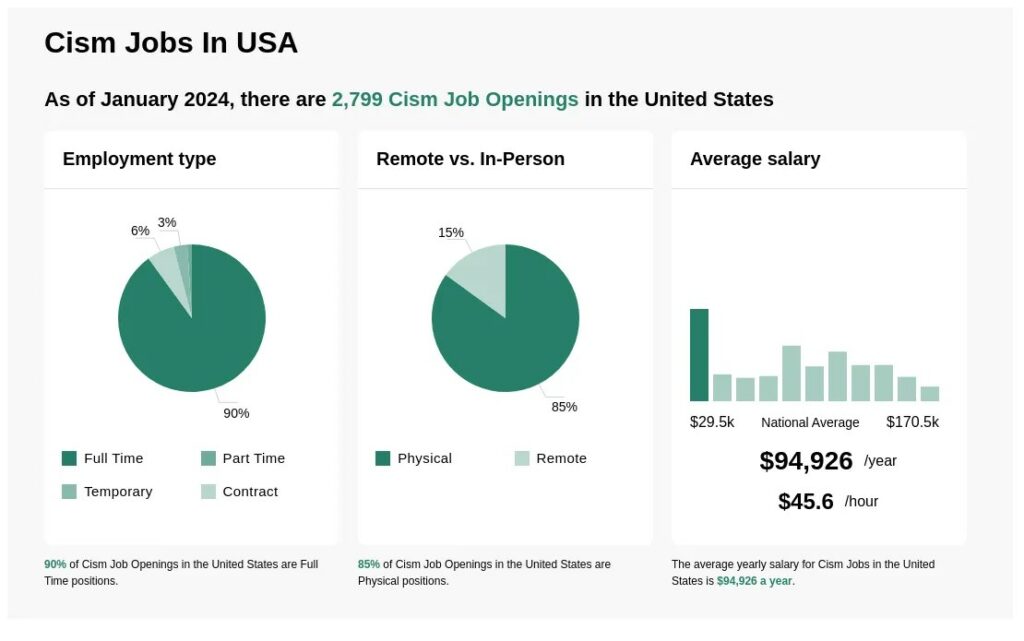
Image source: www.ziprecruiter.in
Skills required to be a CISM professional
- A deep understanding of how information systems work, including their infrastructure, applications, operations, and security measures. They should be able to delve into technical details.
- Knowledge about IT governance, frameworks, controls, and auditing standards.
- Skills in assessing risks, analyzing data, and researching to find weaknesses and areas where compliance may be lacking.
- The ability to understand and interpret regulations, and then turn those requirements into auditing procedures.
- Strong written and verbal communication skills to explain findings and recommendations clearly.
- Expertise in audit techniques such as collecting evidence, conducting interviews, testing controls, and documenting results.
- Strong analytical thinking and attention to detail are critical for evaluating audit evidence and figuring out the underlying causes of issues.
CISM Salary Structure
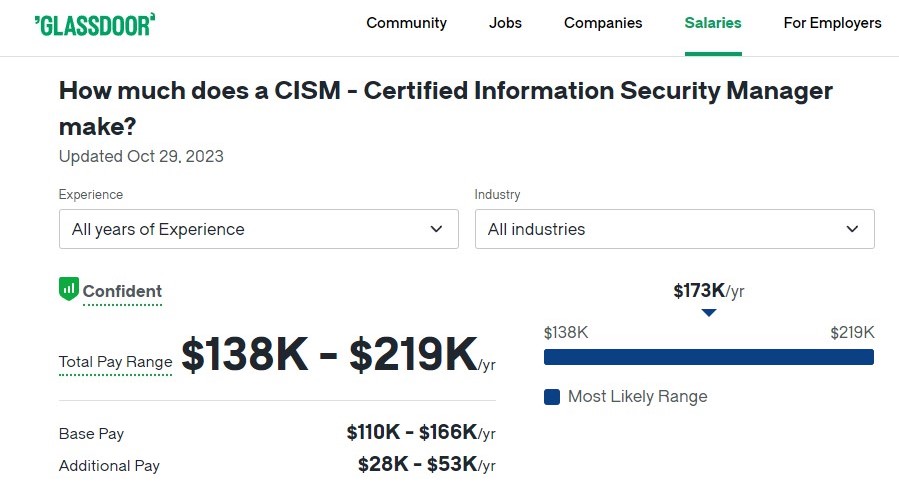
According to Glassdoor, The average annual salary for a CISM – Certified Information Security Manager in the United States area is approximately $135,001, with an estimated total pay of $172,577 per year. These figures are based on our proprietary Total Pay Estimate model, using salary data gathered from our users. The additional estimated pay amounts to around $37,576 annually. This additional pay may include cash bonuses, commissions, tips, and profit sharing. The “Most Likely Range” indicates values falling within the 25th and 75th percentiles of all available pay data for this position.
CISA vs CISM: Which one to choose and Why?
When deciding between pursuing the CISA or CISM certification, several factors should be taken into account:
- Current job role and experience: If you’re in an auditing or risk assessment-focused position, CISA may be more suitable. For management and governance-oriented roles, CISM is a better fit.
- Career Path: Consider whether you aim to advance into IT audit leadership or move into a security/risk management leadership role. CISA is ideal for the former, while CISM is preferred for the latter.
- Employer Preferences: Some employers have a preference for either CISA or CISM-certified professionals. Research whether there’s a strong preference in your desired workplace.
- Salary Required: Both certifications offer potential salary increases, but compare typical pay for CISA versus CISM roles to determine which may offer greater earning potential.
- Areas to focus on: CISA emphasizes auditing, governance, and compliance, while CISM covers security program management, risk management, and incident response. Choose the certification that aligns with the skillset you wish to develop.
- Exam difficulty: CISM is widely regarded as highly challenging, whereas CISA is still challenging but somewhat less rigorous. Assess your readiness for each exam.
- Certification cost: Evaluate the costs associated with study materials, preparatory courses, exam fees, and maintenance fees for each certification. The CISM certification cost is USD 575 for ISACA members and USD 760 for non-ISACA members. Members of ISACA pay $575, while non-ISACA members pay $760 for the CISA exam.
- Maintenance requirements: Both certifications mandate 20 hours of continuing education annually. Ensure that you can fulfill this obligation before making your decision.
Conclusion
To wrap up, both the CISA certification and CISM certification offer valuable skills for professionals in information security and IT auditing. CISA focuses on auditing and controlling information systems, while CISM specializes in managing security programs. Both certifications lead to higher salary potential and leadership roles, making them essential for career advancement in today’s digital age.
